Hello aspiring Ethical Hackers. In this blogpost, you will learn about session hijacking. In March 2023, the YouTube channel of youtuber Linus Sebastian was hacked. Hackers deleted all his videos and uploaded a few videos on crypto currency. It was later discovered that hackers used session hijacking to gain access to Linus Sebastian YouTube channel. With the advent of passkeys, biometric and password less authentication, hackers are finding it difficult to grab credentials using password cracking. So, they are increasingly turning their attention towards session hijacking. What is session hijacking? To understand that you need to first understand what a session is.
What is a Session?
You login into a number of websites daily. You should have noticed that you don’t have to login again and again into some of the websites. I mean you are kept in logged in state on a website and you don’t have to enter your username and password again and again.
How is this possible? Well, HTTP & HTTPS are itself stateless and hence sessions are used by almost all the webservers to keep the user logged in and track him. A session is assigned as soon as user logs in and it is kept active for a particular period of time or until the user decides to log out.
What is a Session ID?
These active sessions are tracked using piece of text called a Session ID. Usually Session ID is included as part of a cookie.
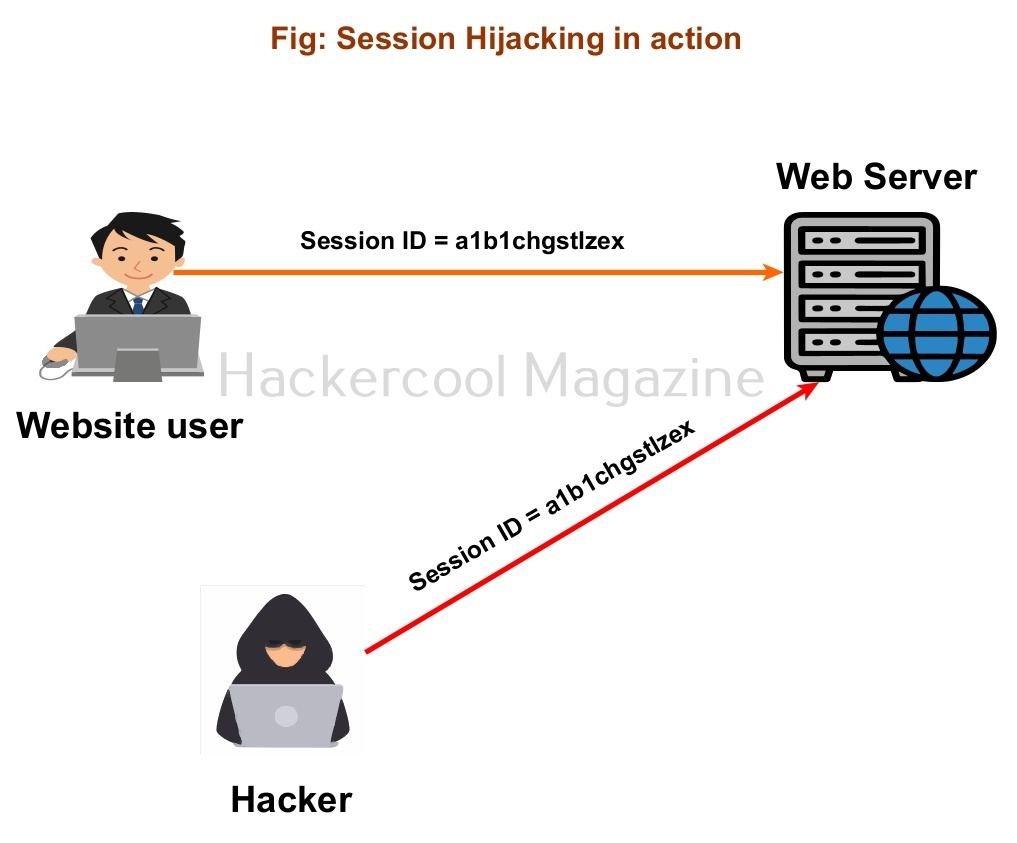
What is Session Hijacking?
A session hijacking or cookie hijacking is the stealing of a session by whatever means. Once a hacker steals a session, he can perform all actions a legitimate user of that account can perform. No need to crack passwords anymore.
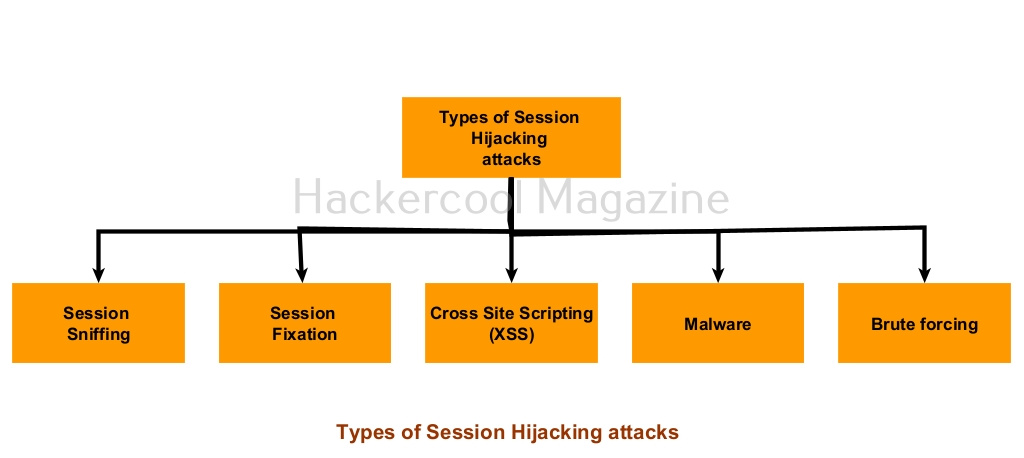
Types of Session Hijacking
1. Session Fixation:
In a Session fixation attack, the attacker tries to fix the session ID for another user. This is only possible if the webserver accepts Session ID’s from URL.
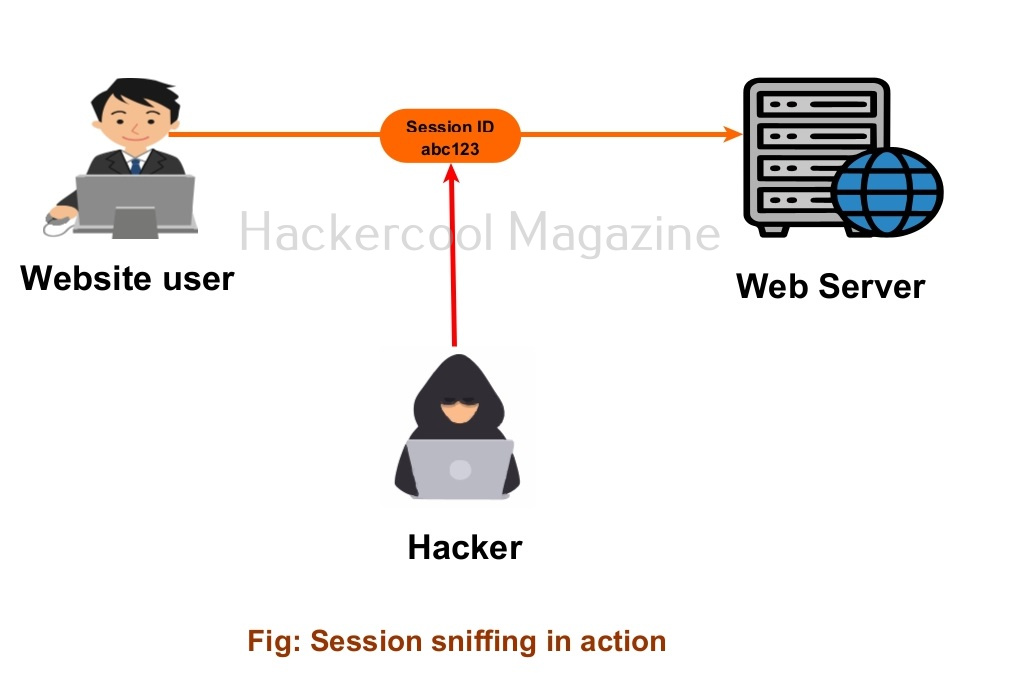
2. Session sniffing:
In packet sniffing and password sniffing, you learnt how hackers can sniff the data in transit. Not just these, even session IDs can be sniffed using any packet sniffer like Wireshark, tcpdump, Ettercap, dsniff, kismet and driftnet etc. This is done by sniffing on cookies if they are being transmitted without any encryption as they contain the session IDs.
3. Cross Site Scripting (XSS):
In our previous article you learnt about Cross Site Scripting. Hackers can also use it to steal a session ID.
4. Malware:
Hackers can install session hijacking malware on the victim’s computer and steal the session ID. Learn more about malware.
5. Brute forcing:
Not just credentials, even session ID’s can be brute forced by hackers. However, they need to have some knowledge about the structure of the session ID before attempting brute force.
Follow Us