Hello aspiring ethical hackers. In this article, you will learn about the ProxyLogon vulnerability. ProxyLogon is a vulnerability that impacts the Microsoft Exchange Server. It is estimated that over 2,50,000 Microsoft Exchange Servers were victims of this vulnerability at the time of its detection.
The Proxy Logon vulnerability is related to the four zero day vulnerabilities that were detected in the Exchange Server in December 2020. On December 10, 2020, Orange Tsai, security researcher working in DEVCORE, discovered that attackers can combine some vulnerabilities in the Exchange Server to achieve remote code execution on the target and upload a webshell to it. The four vulnerabilities are,
CVE-2021-26855: SERVER SIDE REQUEST FORGERY
This is a Server-Side Request Forgery (SSRF) vulnerability in the Exchange Server that allows remote attackers to gain admin access once exploited. This can be exploited by sending a specially crafted web request to a vulnerable Exchange Server. The web request contains an XML SOAP payload directed at the Exchange Web Services (EWS) API endpoint. This request bypasses authentication using specially crafted cookies. This vulnerability, combined with the knowledge of a victim’s email address, means the attacker can exfiltrate all emails from the target’s Exchange mailbox.
CVE-2021-26857: REMOTE CODE EXECUTION VULNERABILITY
This is a post-authentication insecure deserialization vulnerability in the Unified Messaging service of an Exchange Server that allows commands to be run with SYSTEM privileges. The SYSTEM account is used by the operating system and services that run under Windows. As readers have seen many times in our Magazine, a SYSTEM account in Windows has full permissions by default. A hacker can either steal credentials or use the above mentioned vulnerability to execute arbitrary commands on a vulnerable Exchange Server in the security context of SYSTEM.
CVE-2021-26858 AND CVE-2021-27065
These two vulnerabilities are post-authentication arbitrary file write vulnerabilities that allow attackers to write files to any path on a vulnerable Exchange Server. A malicious hacker can also exploit the previously mentioned SSRF vulnerability to achieve admin access and then exploit this vulnerability to write web shells to virtual directories (VDirs). These virtual directories are published to the internet by the server’s Internet Information Server (IIS).
IIS is Microsoft’s web server and a dependency that is installed with Exchange Server and provides services for Outlook on the web, previously known as Outlook Web Access (OWA), Outlook Anywhere, ActiveSync, Exchange Web Services, Exchange Control Panel (ECP), the Offline Address Book (OAB) and AutoDiscover.
According to Microsoft, these vulnerabilities were first exploited by HAFNIUM, a Chinese government sponsored APT (Advanced Persistent Threat) but operating out of China. This group is known to install the web shell named China Chopper. As of 12th March 2021, at least 9 other hacker groups exploited these vulnerabilities apart from HAFNIUM. The versions of Exchange Servers vulnerable to these vulnerabilities are,
Exchange Server 2019 < 15.02.0792.010
Exchange Server 2019 < 15.02.0721.013
Exchange Server 2016 < 15.01.2106.013
Exchange Server 2013 < 15.00.1497.012
The exploit is named Proxy Logon as it exploits the proxy architecture and login mechanism in the Exchange Server.
How to detect ProxyLogon vulnerability?
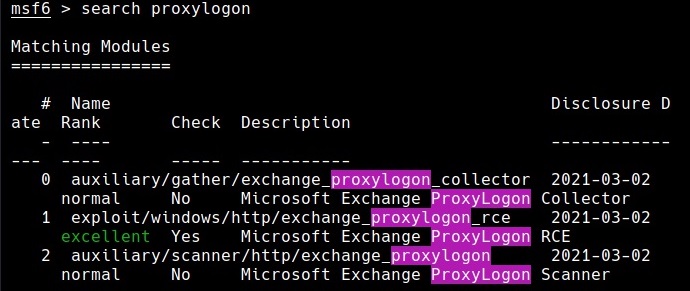
Metasploit has some modules related to these vulnerabilities. Let’s have a look at these modules.
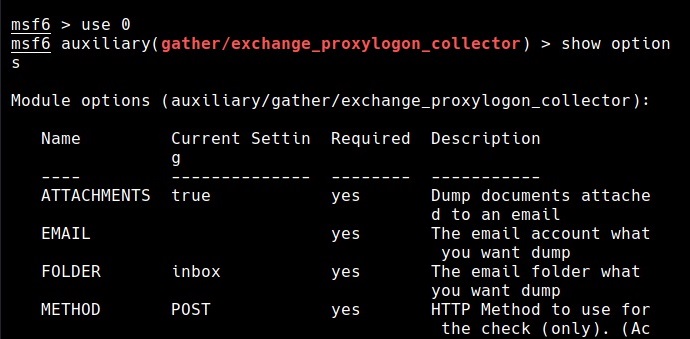
The auxiliary/gather/exchange_proxylogon_collector module exploits the CVE-2021-26855 vulnerability and dumps all the contents of the mailboxes.
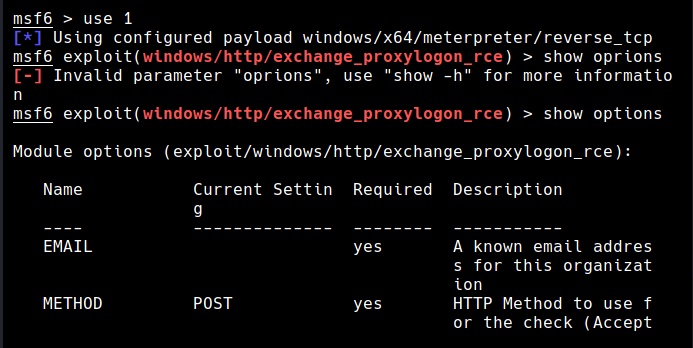
The exploit/windows/http/exchange_proxylogon_rce module exploits the CVE-2021-26855 vulnerability to bypass authentication and gain admin access and then writes a arbitrary file to the target using CVE-2021-27065 to achieve remote code execution. All the above mentioned versions are vulnerable by default.
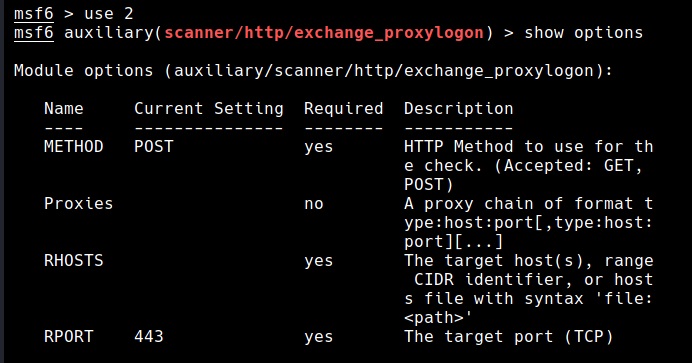
The auxiliary/scanner/http/exchange_proxylogon module checks for the CVE-2021-26855 vulnerability that makes Exchange Servers vulnerable.
Microsoft has released a security update on March 2021 to patch these vulnerabilities in Exchange Server versions mentioned above. Applying these patches will fix these vulnerabilities. As soon as Microsoft released these security updates, hacker groups around the world went on a scanning spree to hunt for unpatched Exchange Servers.
As there was a delay in applying patches, Microsoft also released a one-click mitigation tool that fixed these vulnerabilities in Exchange Servers. Microsoft has also noted that this tool named Microsoft Exchange On-Premises Mitigation Tool (EOMT) is helpful for those organizations that don’t have a dedicated IT security staff. This tool also includes the Microsoft Safety Scanner and an URL Rewrite mitigation for CVE-2021-26855. However, it stressed that this tool was not an alternative for applying the released security patches.