Hello, aspiring ethical hackers. In our previous blogpost, you learnt about vulnerability scanning. In this article you will learn about vulnerability assessment.
What is vulnerability assessment?
Vulnerability assessment (VA) is sometimes interchangeably used with vulnerability scanning but is entirely different form vulnerability scanning. VA is a systematical review of vulnerabilities or weaknesses in a system or a network or even in an entire company. While vulnerability scanning is just scanning for vulnerabilities, Vulnerability assessment also assigns security levels to the vulnerabilities identified and suggests remediation or mitigation if needed.
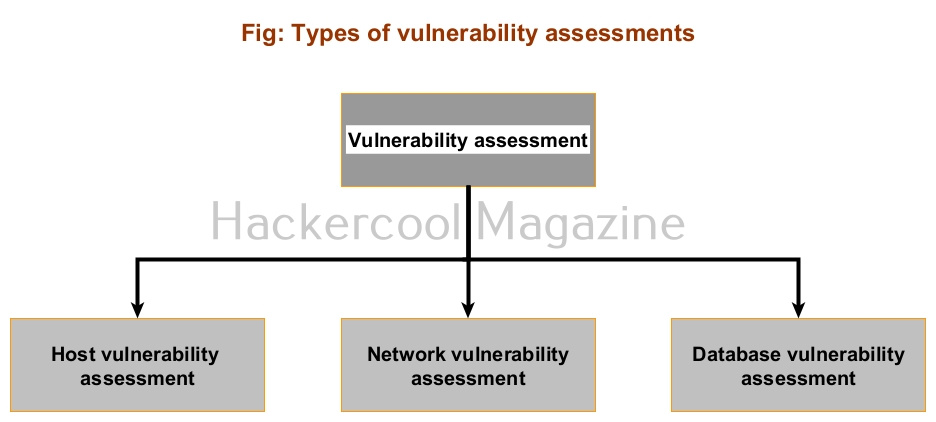
Types of vulnerability assessments
As vulnerability assessment has a larger scope, there are different types of vulnerability assessments. They are,
1. Host assessment:
When a single host or a system (which can include server or client) is assessed for vulnerabilities, it is called host assessment.
2. Network assessment:
When vulnerabilities in an entire network are assessed, it is known as network VA. This can include all the devices, gateways and servers in the entire network.
3. Database assessment:
When vulnerabilities of a database are assessed, it is known as a database assessment.
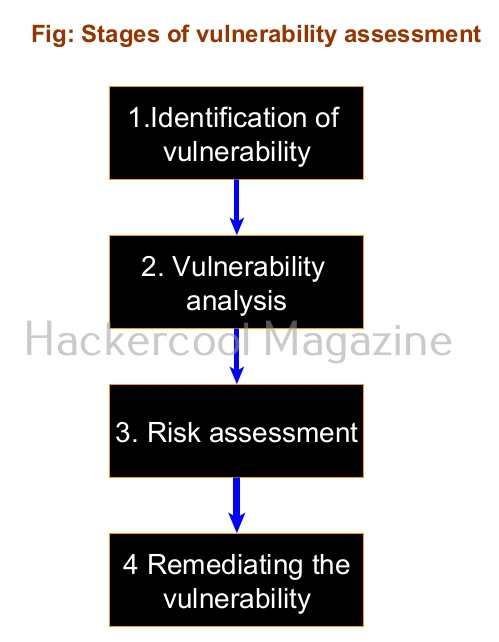
Stages of a vulnerability assessment
VA primarily consists of four stages. They are,
1. Vulnerability identification:
The first stage of the VA is to identify the vulnerabilities in a host network or any other resources. This involves scanning for vulnerabilities using automated tools.
2. Vulnerability analysis:
The second stage is to analyze the vulnerability identified. This includes identifying the source of and cause of the vulnerabilities.
3. Risk assessment:
The third stage in VA includes assessing the risk of the vulnerability. In this stage, a rank or security level is given to each vulnerability detected. This rank depends on the severity of the vulnerability, how simple it is to exploit this vulnerability, ease of access, and what a hacker can get if he is successful in exploiting it.
4. Remediation:
The final step of VA is to fix or remediate the vulnerability. This stage can include developers, operation teams and cybersecurity professionals.
Some of the tools that can be used to perform vulnerability assessment are Nessus, OpenVAS, Burp suite, Nikto, Wireshark etc.