Hello, aspiring Ethical Hackers. In our previous blogpost, you studied what is a vulnerability and different types of vulnerability scanning. In this blogpost, you will learn how is vulnerability scoring given and how are vulnerabilities scored.
What is vulnerability scoring?
Every time a vulnerability is identified or detected, its severity is needs to be estimated to understand the impact of this vulnerability after it is exploited. Based on this severity, a score is given to it.
How is this score given?
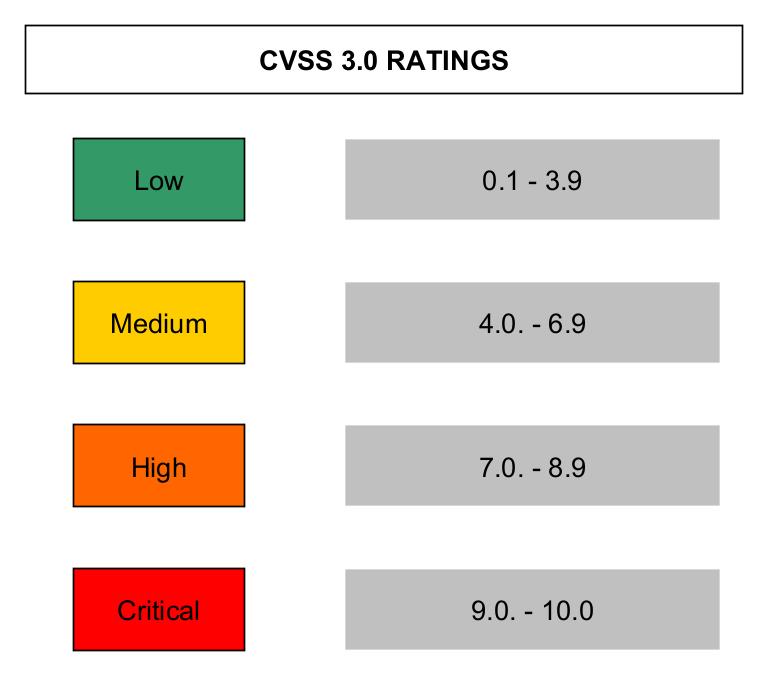
To give this scoring, an open framework named Common Vulnerability Scoring System (CVSS) is used. CVSS provides a numerical representation (ranging from 0 to 10) to the security vulnerability.
CVSS is maintained by the Forum of Incident Response and Security Teams (FIRST), which is a USA based nonprofit organization. Members of this organization come from all around the globe. Cybersecurity professionals of any organization use CVSS scores for vulnerability management and remediating them.
How CVSS scoring works?
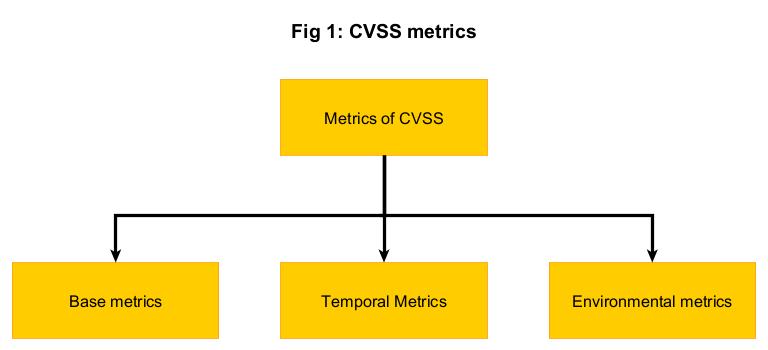
A CVSS score is assigned to a vulnerability by considering three metrics. They are:
A. Base
B. Temporal and
C. Environmental.
A. CVSS Base Metrics
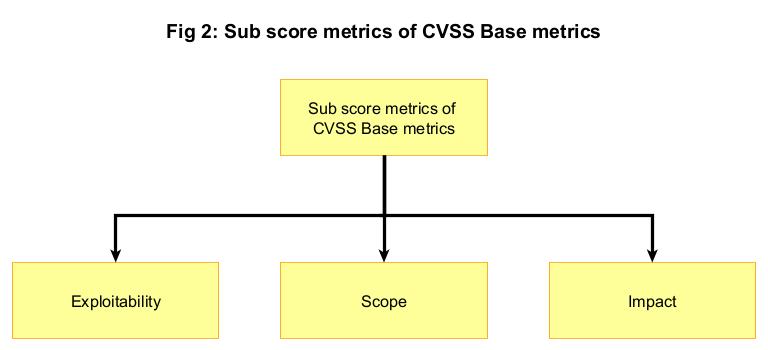
The base metrics of CVSS represent the characteristics of the vulnerability itself. These characteristics never change with time or any protection put in place by any organization to prevent its exploitation. CVSS base metrics comprise of three sub score elements. They are, 1) Exploitability 2) Scope and 3) Impact.
1. Exploitability
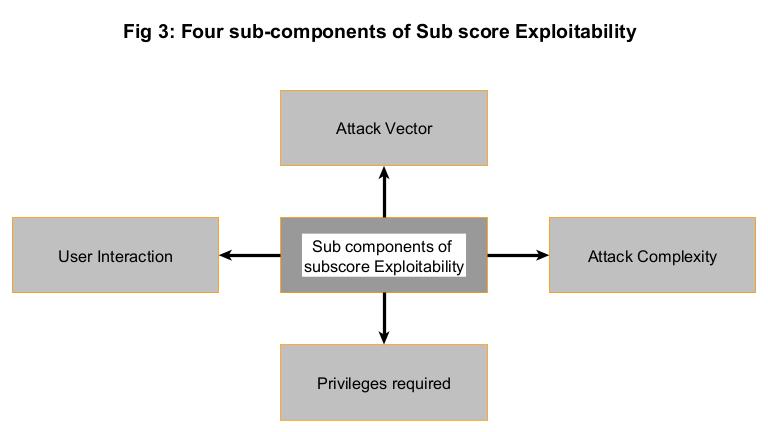
The sub-score exploitability is made up of four sub-components.
i). Attack Vector:
The score of attack vector is based on the level of access that is required to exploit the vulnerability. If the vulnerability can be exploited remotely, the score is higher and if local access is required to exploit the vulnerability, the score is lower. For example, ms08-67 has higher score than malicious USB attack.
ii). Attack Complexity:
This score depends on the additional work that has to be put by attacker to exploit the vulnerability. For example, exploiting EternalBlue does not need any additional work by attacker whereas to performing a Man-In middle attack requires additional work from the attacker. Usually, the additional work the attacker puts depends on factors which are out of control of the attacker.
iii). Privileges required:
This score depends on the privileges required to exploit the particular vulnerability. If the exploitation doesn’t need any credentials or privileges, its score is high and if he needs privileges or authentication, the score is low. For example, Spring4shell vulnerability has higher score then Dirtypipe vulnerability
iv). User Interaction:
This score depends on the level of user interaction needed to exploit the vulnerability. If the attacker can exploit a vulnerability without user interaction, the score is high whereas if attacker needs user interaction the score is low. For example, Heartbleed has higher score than ms14-100, Follina or Macro attack.
2. Scope
The second base metric of CVSS is “Scope” which relates to the reach of the vulnerability. In simple words, when a vulnerability in a component is exploited, does it affect other components? If exploitation of vulnerability in one component affects the operating system or a database, the CVSS score is higher and in the opposite case, it is lower. For example, SQL injection has higher score than Cross Site scripting.
3. Impact
Impact is the actual affect that occurs when a vulnerability is exploited. The sub metric “Impact” has three sub-components. They are: Confidentiality, Integrity and Availability.
i). Confidentiality:
This score depends on the amount of data the attacker gains access to after exploiting the vulnerability. The score is higher if all the data on the exploited system is accessed by attacker and lower if little to no data is accessed.
ii). Integrity:
This score depends on the ability of attacker to make changes on the system by exploiting a particular vulnerability. If the attacker can completely alter the exploited system, this score is high and if he can make few or no changes at all, this score is low.
iii). Availability:
This score depends on the availability of the system to authorized users after being exploited. If a system is not accessible to authorized users after exploitation, the score is high.
B. CVSS Temporal Metrics
The meaning of English word “Temporal” is temporary or constantly changing. Similarly, the CVSS temporal metrics of a vulnerability constantly change.
When a vulnerability is just disclosed, the chances of some one exploiting it are there but a little low. When a Proof-Of-Concept (POC) exploit is released, the chances increase, sometimes exponentially, As the POC exploit is further improved, the chances increase more. As patches and fixes are released, the exploitation attempts fall. As you can see the exploitation of a vulnerability constantly changing with time. CVSS Temporal metrics have three sub-components. They are, Exploit code maturity, Remediation level and Report Confidence.
1. Exploit code maturity
As the code of the exploit of the vulnerability becomes more stable and widely available, this score will increase.
2. Remediation Level
This score is more when the vulnerability is discovered, but as fixes and patches are applied this score keeps decreasing. If the vulnerability is fixed completely, this score decreases further.
3. Report confidence
This sub metric measures the level of validation that demonstrates that a vulnerability is valid and can be exploited by attackers.
C. CVSS Environmental Metrics
Environmental metrics of CVSS are used to allow an organization to modify the base CVSS score based on security Requirements and modification of Base metrics.
1. Security requirements
Security Requirements are used to characterize the asset in which a vulnerability is reported. For example, a vulnerability affecting the database server gets higher score that a vulnerability in a software being used on one of the workstations by an employee of the organization.
2. Modified Base Metrics
An organization or company changes the values of the Base CVSS metrics after putting some fixes, mitigations or patches. For example, we have discussed some vulnerabilities above which can be exploited remotely. If the system having that vulnerability is disconnected from the internet, the score can be decreased.
That’s how vulnerability scoring is assigned to vulnerabilities.
Follow Us