Hello aspiring ethical hackers. In one of our previous blogposts, you have learnt what is wifi hacking, types of WiFi hacking attacks etc. In this blogpost, you will learn how to crack WPA/ WPA2 password with a tool called Fern WiFi cracker.
Fern Wifi Cracker is a Wireless security auditing and attack software program written in Python. It can crack and recover WEP/WPA/WPS keys and also run other network based attacks on wireless or ethernet based networks.
As already explained, WPA stands for Wifi Protected Access. It is an encryption system to secure WLAN networks. It eliminates all known vulnerabilities in WEP(Wired Equivalent Privacy). WPA uses 128 bit key and 48 bit initialization vector while WEP uses 108 bit key with 24 bit initialization vector. WPA2 is the successor of WPA. Both WPA and WPA2 use temporal key integrity protocol(TKIP) for encryption and pre-shared key(PSK) authentication. The only difference between WPA and WPA2 is that they use Rivest Cipher(RC4) and Advanced Encryption Standard(AES) encryption algorithms respectively. Both can be configured to use counter cipher block chaining mode(CCM) though. They are by far considered most secure for Wifi networks.
So today we are learn cracking WPA/WPA2 passwords using a GUI tool also inbuilt in Kali Linux, Fern Wifi cracker. Open the tool, Fern Wifi cracker.
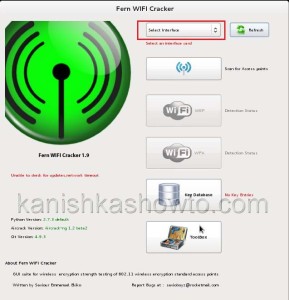
Select our wireless interface WLAN). Click on the tab “Scan for access points”. The tool will search for available access points as shown below.
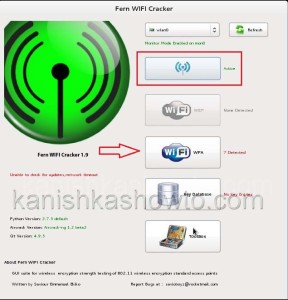
Since we want to hack a WPA enabled wifi network, click on WPA tab. It will show all the available WPA enabled networks.
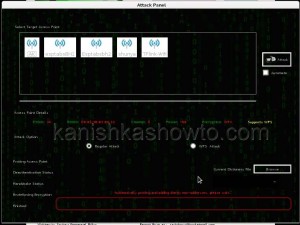
Click on the wifi network whose password we want to crack( in my case “shunya”). Browse to the dictionary file we want to choose as shown below.
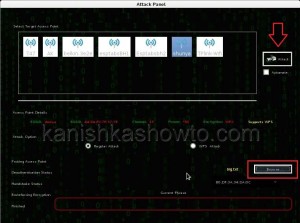
Click on “Wifi attack” tab. The tool will automatically crack the password for you as shown below.
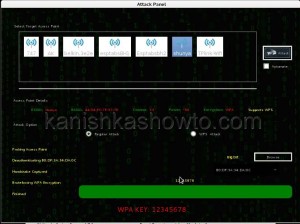
Hope this was helpful. Learn how to crack WiFi passwords with aircrack.
Follow Us
