Hello, aspiring ethical hackers. In our previous blogpost on Wifi hacking, you learnt about what is a evil twin attack. In this article, you will learn about wifiphisher. Wifi phisher is a rogue access point and evil twin creation framework for conducting wireless security testing. Let’s see how this tool works. For this, we will be using Kali Linux as wifiphisher is available by default in its repositories. We will also be needing a wireless adapter that can monitor wireless packets. I am using ALFA AWVS036NHA adapter for this article.
Note that Wifi phisher needs root privileges to work.
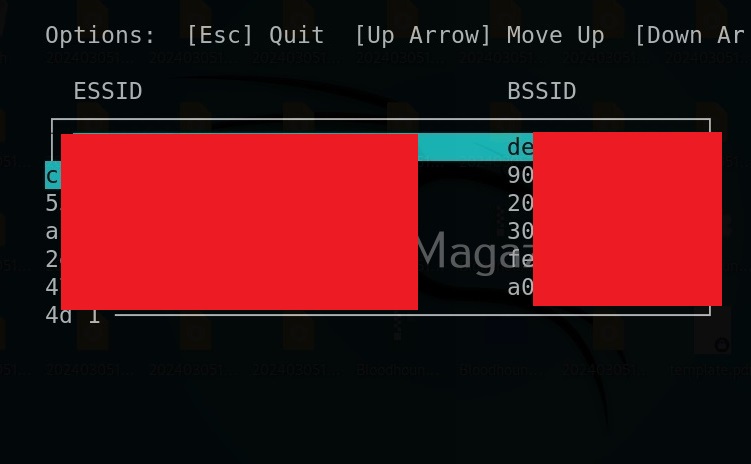
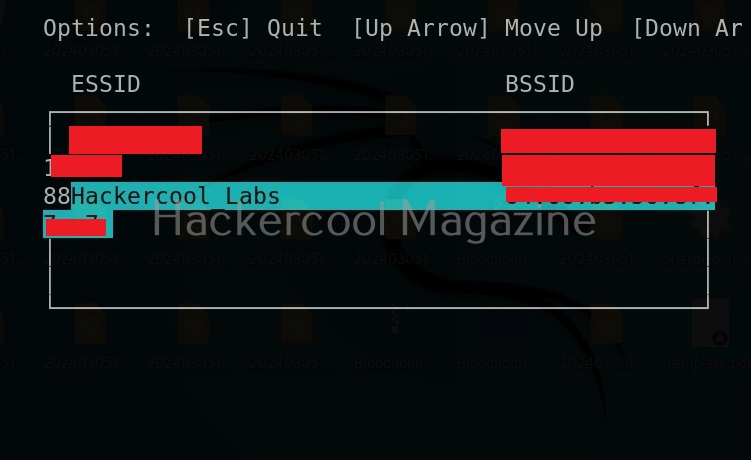
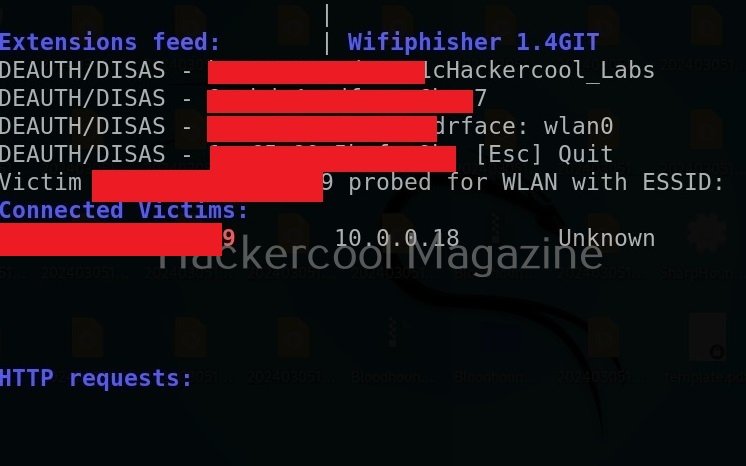
After starting, wifi phisher starts scanning for all the access points it can detect.
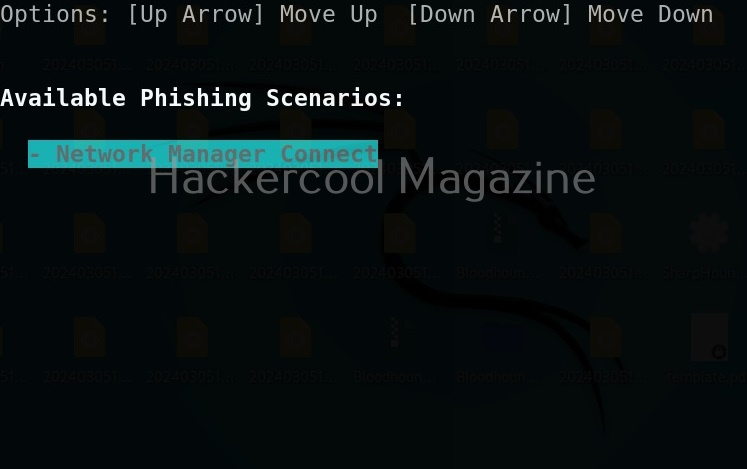
Select the wifi access point you want to target. For example, here I select “Hackercool Labs”. Then, this tool will display the available phishing scenarios (Actually, there’s only one here). Select it.
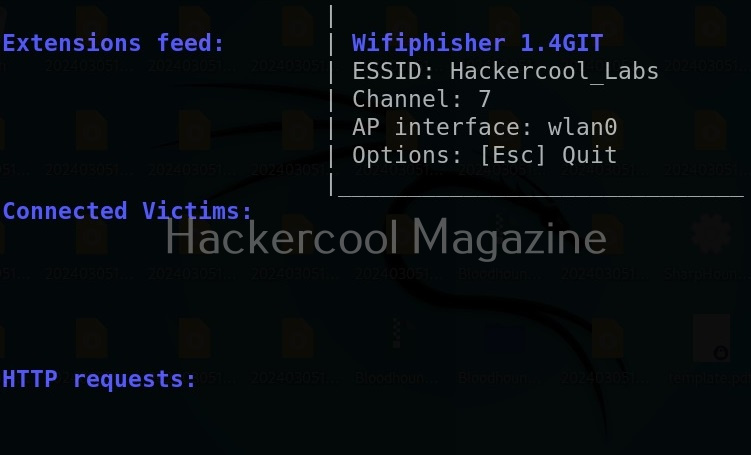
Then this tool will create a evil twin of this network.
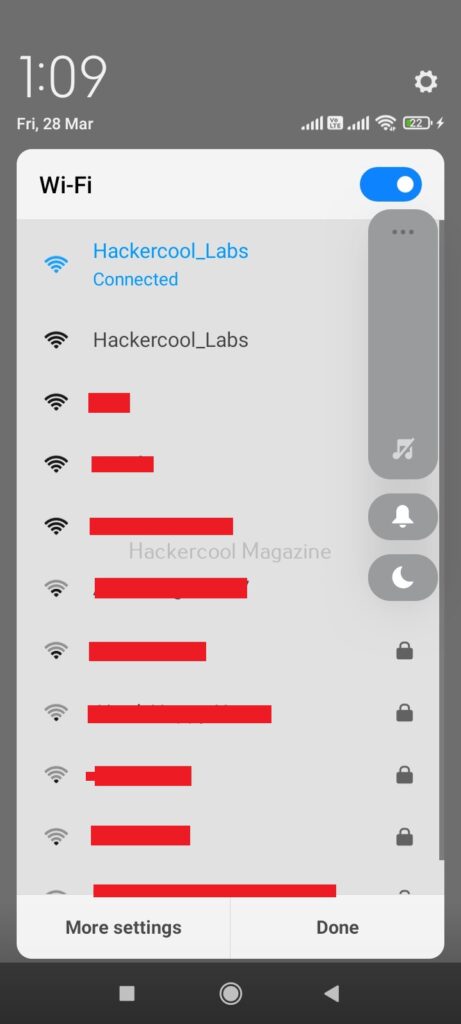
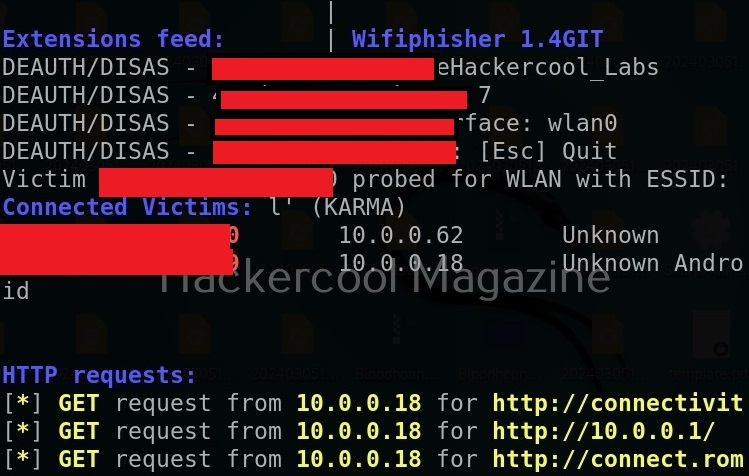
This is how it looks for any client or users trying to to connect to “Hackercool_Labs” access point.
Wifi phisher tries to de-authenticate all clients connected to the genuine access point.
You can see the connected clients.
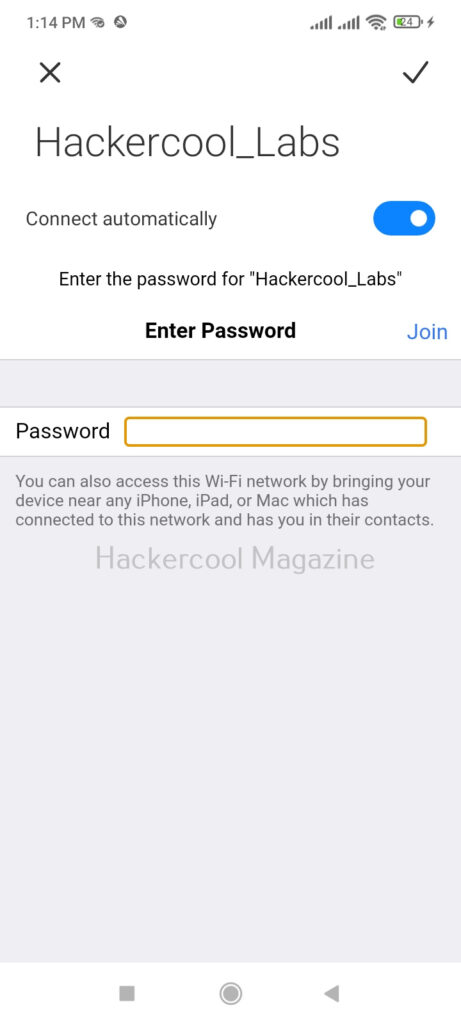
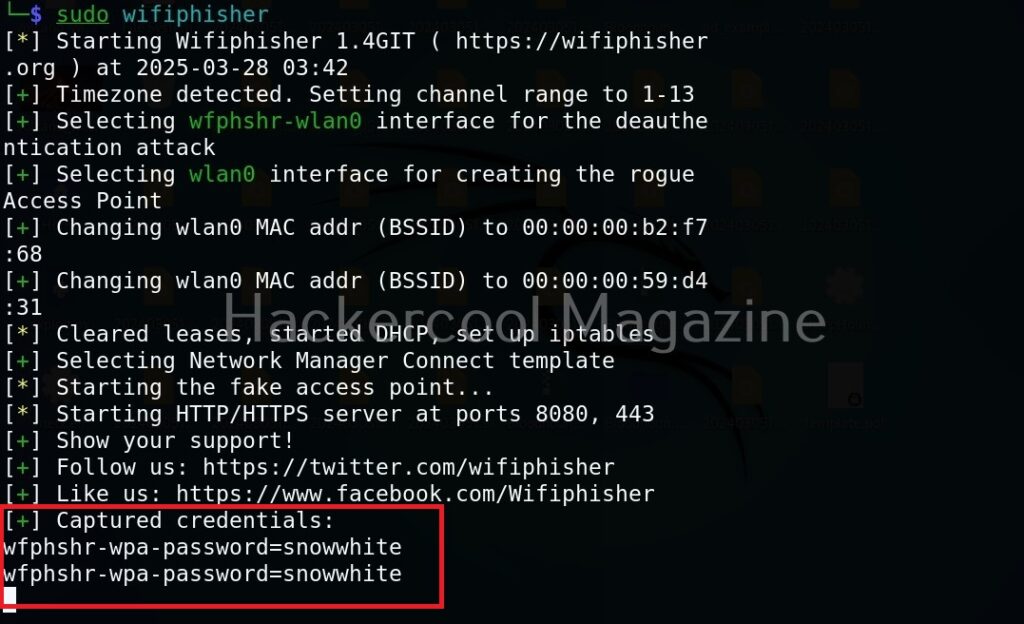
When any of the clients tries to connect to the evil twin instead of genuine access point, he will be asked to type password of the genuine access point as shown below.
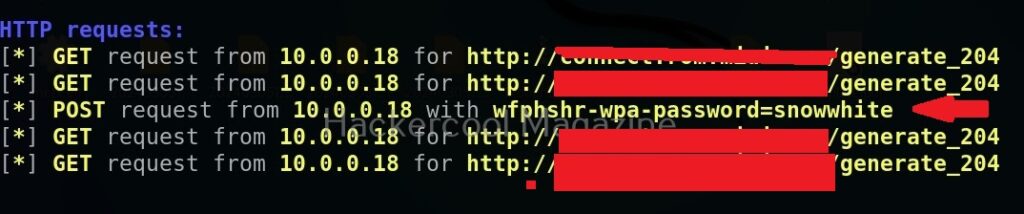
Wifi phisher will log all HTTP requests. So you can see password the user is typing.
Next, learn about wifipumpkin, another powerful wifi rogue access point framework.
Follow Us